How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer.
CCNA 1 – ITN Pretest Exam Answers
1. Convert the decimal number 231 into its binary equivalent. Select the correct answer from the list below.
- 11110010
- 11011011
- 11110110
- 11100111
- 11100101
- 11101110
2. Convert the binary number 10111010 into its hexadecimal equivalent. Select the correct answer from the list below.
- 85
- 90
- BA
- A1
- B3
- 1C
3. The failure rate in a certain brand of network interface card has been determined to be 15%. How many cards could be expected to fail in a company that has 80 of the cards installed?
- 8
- 10
- 12
- 15
4. A local real estate company can have its 25 computer systems upgraded for $1000. If the company chooses only to upgrade 10 systems, how much will the upgrade cost if the same rate is used?
- $100
- $200
- $400
- $500
- $600
5. Considering the average capacity of storage device media, drag the storage media on the left to the capacity list on the right.
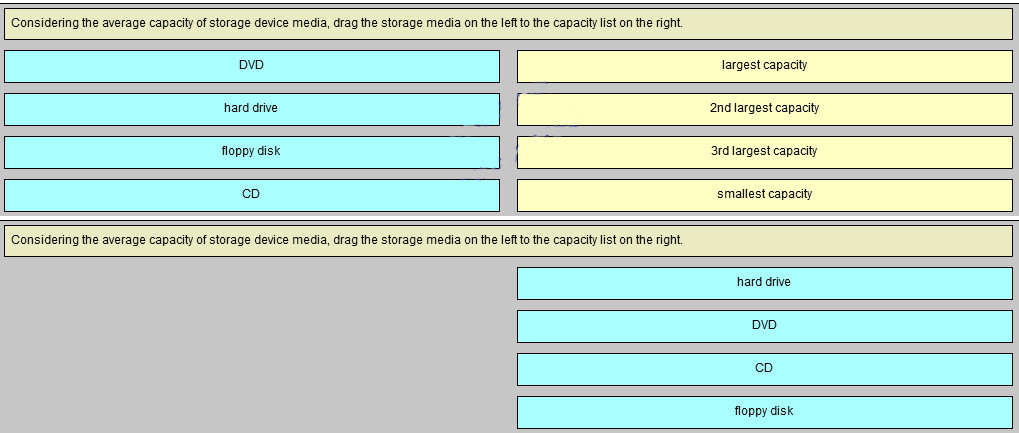
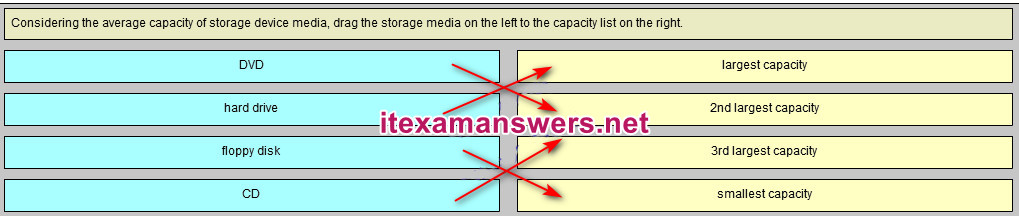
6. Which two devices provide permanent data storage? (Choose two.)
- Blu-Ray disc
- hard drive
- keyboard
- monitor
- RAM
7. If a technician uses an average of 2 cans of compressed air per week for cleaning, how many cans should be ordered for 8 technicians over the next 10 weeks?
- 16
- 20
- 80
- 160
- 200
8. What is a function of the BIOS?
- enables a computer to connect to a network
- provides temporary data storage for the CPU
- performs a power-on self test of internal components
- provides graphic capabilities for games and applications
9. Match the form of network communication with its description. (Not all options are used.)
- Question and Answer:
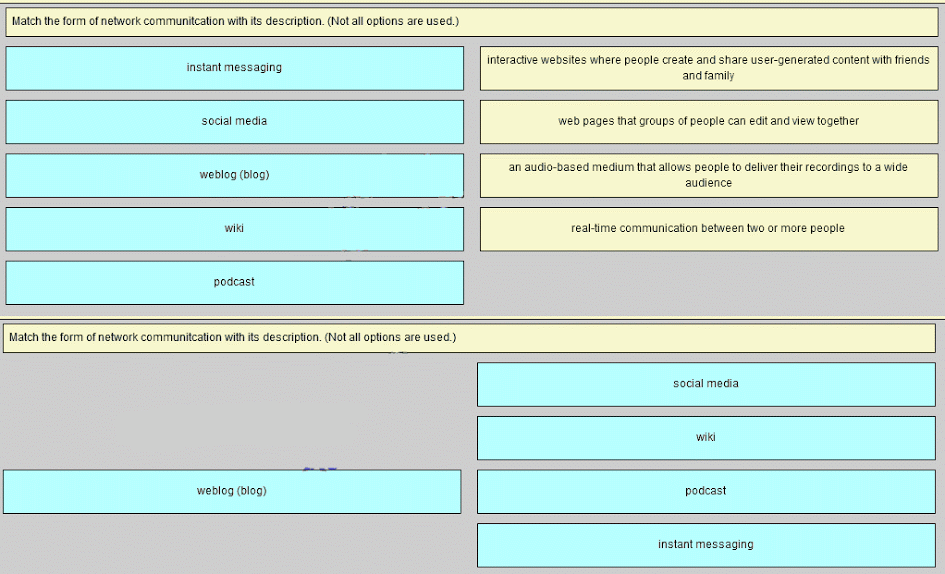
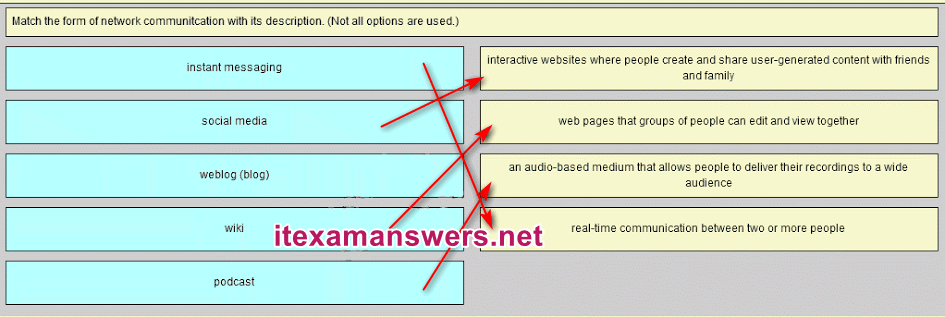
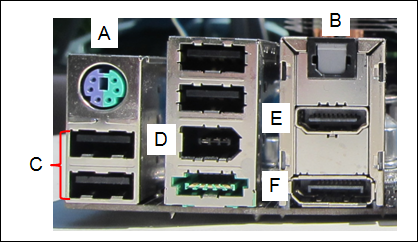
10. Refer to the exhibit. Match the port to the associated letter shown in the exhibit. (Not all options are used.)
- Question and Answer:

11. Which is a characteristic of the Internet?
- It is not centrally governed.
- It uses only physical addresses.
- It uses private IP addressing.
- It is localized to specific geographic locations.
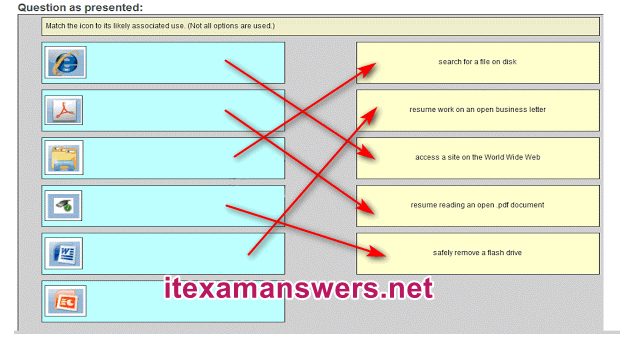
12. Match the icon to its likely associated use. (Not all options are used.)
13. Which command can be used to test connectivity between two computers that are attached to a network?
- ipconfig
- ping
- winipcfg
- ifconfig
- nbtstst -s
14. A person-hour is the amount of work that the average worker can do in one hour. It is anticipated that a company-wide system upgrade will take approximately 60 person-hours to complete. How long will it take five technicians to perform the refresh?
- 5 hours
- 8 hours
- 10 hours
- 12 hours
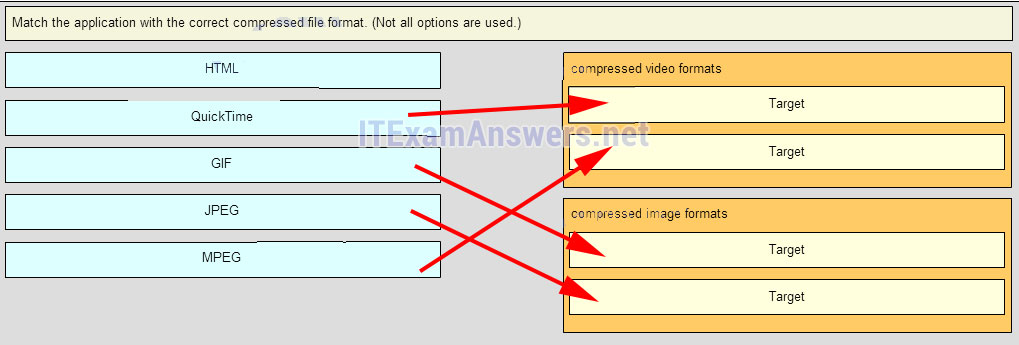
15. Match the application with the correct compressed files format. (Not all options are used.)
- Question and Answer:
16. Which type of connector does a network interface card use?
- DIN
- PS-2
- RJ-11
- RJ-45
17. A user is having problems accessing the Internet. The command ping www.cisco.com fails. However, pinging the IP address of cisco.com with the command ping 198.133.219.25 is successful. What is the problem?
- The web server is down.
- The default gateway is incorrect.
- There is a problem with DNS.
- The address of the ARP cache is incorrect.
18. Which option shows the proper notation for an IPv6 address?
- 2001,0db8,3c55,0015,abcd,ff13
- 2001-0db8-3c55-0015-abcd-ff13
- 2001.0db8.3c55.0015.abcd.ff13
- 2001:0db8:3c55:0015::abcd:ff13
19. What is the purpose of the routing process?
- to encapsulate data that is used to communicate across a network
- to select the paths that are used to direct traffic to destination networks
- to convert a URL name into an IP address
- to provide secure Internet file transfer
- to forward traffic on the basis of MAC addresses
20. Which device should be used for enabling a host to communicate with another host on a different network?
- switch
- hub
- router
- host
21. A home user is looking for an ISP connection that provides high speed digital transmission over regular phone lines. What ISP connection type should be used?
- DSL
- dial-up
- satellite
- cell modem
- cable modem
22. A company is expanding its business to other countries. All branch offices must remain connected to corporate headquarters at all times. Which network technology is required to support this requirement?
- LAN
- MAN
- WAN
- WLAN
23. Why would a network administrator use the tracert utility?
- to determine the active TCP connections on a PC
- to check information about a DNS name in the DNS server
- to identify where a packet was lost or delayed on a network
- to display the IP address, default gateway, and DNS server address for a PC
24. Which basic process is used to select the best path for forwarding data?
- routing
- switching
- addressing
- encapsulation
25. Which wireless security procedure should be used to hide the WLAN ID from wireless clients?
- Configure WEP only on the access point.
- Install WAP on the wireless clients.
- Configure MAC address filtering on the access point.
- Disable the broadcast of the SSID on the access point.
- Decrease the antenna spectrum on each wireless client.
26. What is the purpose of having a converged network?
- to provide high speed connectivity to all end devices
- to make sure that all types of data packets will be treated equally
- to achieve fault tolerance and high availability of data network infrastructure devices
- to reduce the cost of deploying and maintaining the communication infrastructure
27. Refer to the exhibit. Consider the IP address configuration shown from PC1. What is a description of the default gateway address?
- It is the IP address of the Router1 interface that connects the company to the Internet.
- It is the IP address of the Router1 interface that connects the PC1 LAN to Router1.
- It is the IP address of Switch1 that connects PC1 to other devices on the same LAN.
- It is the IP address of the ISP network device located in the cloud.
28. Which technology provides a solution to IPv4 address depletion by allowing multiple devices to share one public IP address?
- ARP
- DNS
- NAT
- SMB
- DHCP
- HTTP
29. Which subnet would include the address 192.168.1.96 as a usable host address?
- 192.168.1.64/26
- 192.168.1.32/27
- 192.168.1.32/28
- 192.168.1.64/29
30. A technician uses the ping 127.0.0.1 command. What is the technician testing?
- the TCP/IP stack on a network host
- connectivity between two adjacent Cisco devices
- connectivity between a PC and the default gateway
- connectivity between two PCs on the same network
- physical connectivity of a particular PC and the network
31. Which function is provided by TCP?
- data encapsulation
- detection of missing packets
- communication session control
- path determination for data packets
32. What is the purpose of ICMP messages?
- to inform routers about network topology changes
- to ensure the delivery of an IP packet
- to provide feedback of IP packet transmissions
- to monitor the process of a domain name to IP address resolution
33. What statement describes the function of the Address Resolution Protocol?
- ARP is used to discover the IP address of any host on a different network.
- ARP is used to discover the IP address of any host on the local network.
- ARP is used to discover the MAC address of any host on a different network.
- ARP is used to discover the MAC address of any host on the local network.
34. What is the general term that is used to describe a piece of data at any layer of a networking model?
- frame
- packet
- protocol data unit
- segment
35. Which three IP addresses are private ? (Choose three.)
- 10.1.1.1
- 172.32.5.2
- 192.167.10.10
- 172.16.4.4
- 192.168.5.5
- 224.6.6.6
36. How does a networked server manage requests from multiple clients for different services?
- The server sends all requests through a default gateway.
- Each request is assigned source and destination port numbers.
- The server uses IP addresses to identify different services.
- Each request is tracked through the physical address of the client.
37. Which protocol translates a website name such as www.cisco.com into a network address?
- HTTP
- FTP
- DHCP
- DNS
38. What is an advantage of using IPv6 ?
- more addresses for networks and hosts
- faster connectivity
- higher bandwidth
- more frequencies
39. Refer to the exhibit. Using the network in the exhibit, what would be the default gateway address for host A in the 192.133.219.0 network?
- 192.135.250.1
- 192.31.7.1
- 192.133.219.0
- 192.133.219.1
40. Refer to the exhibit. Host_A is preparing to send data to Server_B. How will Host_A address the packets and frames that will carry this data? (Choose two.)
- The packet destination will be addressed with the IP address of the Router_B interface that is attached to Router_A.
- The frame destination will be addressed with the MAC address of Switch_A.
- The packet destination will be addressed with the IP address of the Router_A LAN interface.
- The frame destination will be addressed with the MAC address of the Router_A LAN interface.
- The packet destination will be addressed with the IP address of Server_B.
- The frame destination will be addressed with the MAC address of Server_B..
41. A network technician is attempting to configure an interface by entering the following command: SanJose(config)# ip address 192.168.2.1 255.255.255.0. The command is rejected by the device. What is the reason for this?
- The command is being entered from the wrong mode of operation.
- The command syntax is wrong.
- The subnet mask information is incorrect.
- The interface is shutdown and must be enabled before the switch will accept the IP address.
42. What protocol is responsible for controlling the size of segments and the rate at which segments are exchanged between a web client and a web server?
- TCP
- IP
- HTTP
- Ethernet
43. A network administrator is troubleshooting connectivity issues on a server. Using a tester, the administrator notices that the signals generated by the server NIC are distorted and not usable. In which layer of the OSI model is the error categorized?
- presentation layer
- network layer
- physical layer
- data link layer
44. Which statement is true about variable-length subnet masking?
- Each subnet is the same size.
- The size of each subnet may be different, depending on requirements.
- Subnets may only be subnetted one additional time.
- Bits are returned, rather than borrowed, to create additional subnets.
45. A wireless host needs to request an IP address. What protocol would be used to process the request?
- FTP
- HTTP
- DHCP
- ICMP
- SNMP
46. What will a host on an Ethernet network do if it receives a frame with a destination MAC address that does not match its own MAC address?
- It will discard the frame.
- It will forward the frame to the next host.
- It will remove the frame from the media.
- It will strip off the data-link frame to check the destination IP address.
47. Which connection provides a secure CLI session with encryption to a Cisco switch?
- a console connection
- an AUX connection
- a Telnet connection
- an SSH connection
48. What are the three ranges of IP addresses that are reserved for internal private use? (Choose three.)
- 10.0.0.0/8
- 64.100.0.0/14
- 127.16.0.0/12
- 172.16.0.0/12
- 192.31.7.0/24
- 192.168.0.0/16
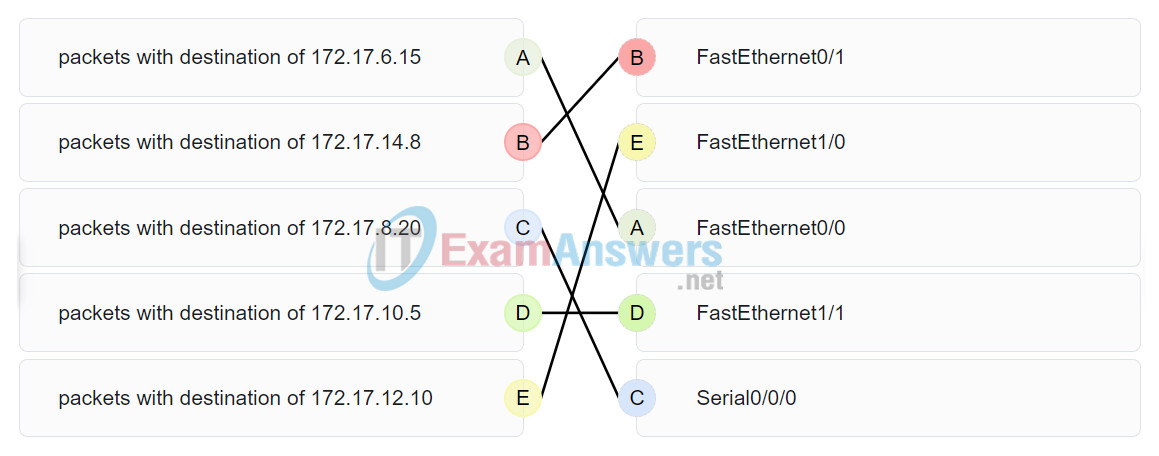
49. Refer to the exhibit. Match the packets with their destination IP address to the exiting interfaces on the router. (Not all targets are used.)
Place the options in the following order:
| packets with destination of 172.17.6.15 | FastEthernet0/0 |
| packets with destination of 172.17.14.8 | FastEthernet0/1 |
| packets with destination of 172.17.12.10 | FastEthernet1/0 |
| packets with destination of 172.17.10.5 | FastEthernet1/1 |
| packets with destination of 172.17.8.20 | Serial0/0/0 |
Answer:
CCNA 1 – ITN Chapter 1 Exam Answers
1. A company is contemplating whether to use a client/server or a peer-to-peer network. What are three characteristics of a peer-to-peer network? (Choose three.)
- better security
- easy to create
- better device performance when acting as both client and server
- lacks centralized administration
- less cost to implement
- scalable
2. Which device performs the function of determining the path that messages should take through internetworks?
- a router
- a firewall
- a web server
- a DSL modem
3. What two criteria are used to help select a network medium from various network media? (Choose two.)
- the types of data that need to be prioritized
- the cost of the end devices utilized in the network
- the distance the selected medium can successfully carry a signal
- the number of intermediary devices installed in the network
- the environment where the selected medium is to be installed
4. Which two statements describe intermediary devices? (Choose two.)
- Intermediary devices generate data content.
- Intermediary devices alter data content.
- Intermediary devices direct the path of the data.
- Intermediary devices connect individual hosts to the network.
- Intermediary devices initiate the encapsulation process.
5. What are two functions of end devices on a network? (Choose two.)
- They originate the data that flows through the network.
- They direct data over alternate paths in the event of link failures.
- They filter the flow of data to enhance security.
- They are the interface between humans and the communication network.
- They provide the channel over which the network message travels.
6. Which area of the network would a college IT staff most likely have to redesign as a direct result of many students bringing their own tablets and smartphones to school to access school resources?
- extranet
- intranet
- wired LAN
- wireless LAN
- wireless WAN
7. An employee at a branch office is creating a quote for a customer. In order to do this, the employee needs to access confidential pricing information from internal servers at the Head Office. What type of network would the employee access?
- an intranet
- the Internet
- an extranet
- a local area network
8. Which two connection options provide an always-on, high-bandwidth Internet connection to computers in a home office? (Choose two.)
- cellular
- DSL
- satellite
- cable
- dial-up telephone
9. Which two Internet connection options do not require that physical cables be run to the building? (Choose two.)
- DSL
- cellular
- satellite
- dialup
- dedicated leased line
10. Which term describes the state of a network when the demand on the network resources exceeds the available capacity?
- convergence
- congestion
- optimization
- synchronization
11. Which expression accurately defines the term bandwidth?
- a method of limiting the impact of a hardware or software failure on the network
- a measure of the data carrying capacity of the media
- a state where the demand on the network resources exceeds the available capacity
- a set of techniques to manage the utilization of network resources
12. Which networking trend involves the use of personal tools and devices for accessing resources on a business or campus network?
- video conferencing
- cloud computing
- BYOD
- powerline networking
13. What is a characteristic of a converged network?
- it provides only one path between the source and destination of a message
- it limits the impact of a failure by minimizing the number of devices affected
- it delivers data, voice, and video over the same network infrastructure
- A converged network requires a separate network infrastructure for each type of communication technology
14. Which statement describes a characteristic of cloud computing?
- A business can connect directly to the Internet without the use of an ISP.
- Applications can be accessed over the Internet by individual users or businesses using any device, anywhere in the world.
- Devices can connect to the Internet through existing electrical wiring.
- Investment in new infrastructure is required in order to access the cloud.
15. Which statement describes the use of powerline networking technology?
- New “smart” electrical cabling is used to extend an existing home LAN.
- A home LAN is installed without the use of physical cabling.
- A device connects to an existing home LAN using an adapter and an existing electrical outlet.
- Wireless access points use powerline adapters to distribute data through the home LAN.
16. What security violation would cause the most amount of damage to the life of a home user?
- denial of service to your email server
- replication of worms and viruses in your computer
- capturing of personal data that leads to identity theft
- spyware that leads to spam emails
17. A user is implementing security on a small office network. Which two actions would provide the minimum security requirements for this network? (Choose two.)
- implementing a firewall
- installing a wireless network
- installing antivirus software
- implementing an intrusion detection system
- adding a dedicated intrusion prevention device
18. Fill in the blank.
A converged network is capable of delivering voice, video, text, and graphics over the same communication channels.
19. Fill in the blank.
The acronym byod refers to the policy that allows employees to use their personal devices in the business office to access the network and other resources.
20. What are two functions of intermediary devices on a network? (Choose two.)
- They are the primary source and providers of information and services to end devices.
- They run applications that support collaboration for business.
- They form the interface between the human network and the underlying communication network.
- They direct data along alternate pathways when there is a link failure.
- They filter the flow of data, based on security settings.
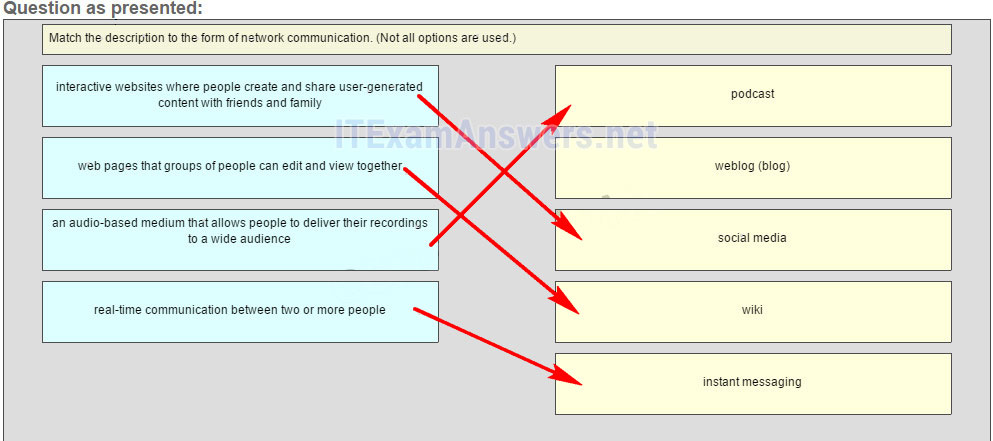
21. Match the description to the form of network communication. (Not all options are used.
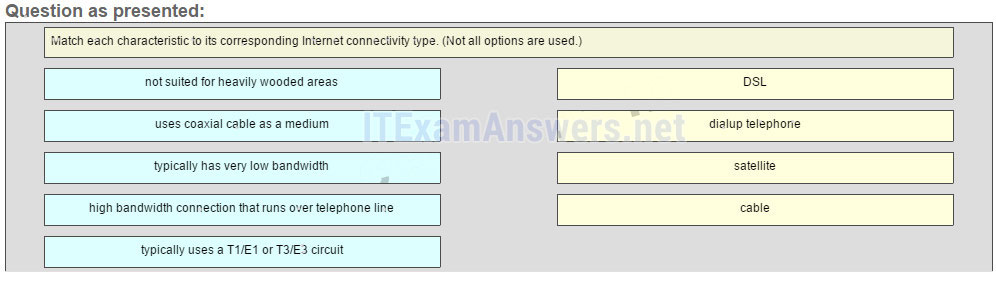
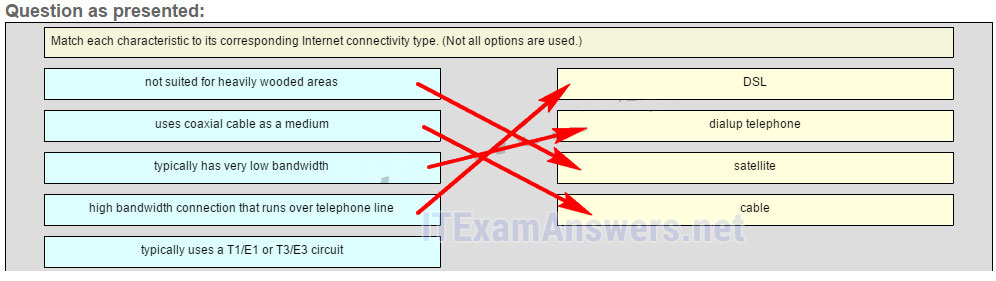
22. Match each characteristic to its corresponding internet conectivity type. (Not all options are used)
23. What is the Internet?
- It is a network based on Ethernet technology.
- It provides network access for mobile devices.
- It provides connections through interconnected global networks.
- It is a private network for an organization with LAN and WAN connections.
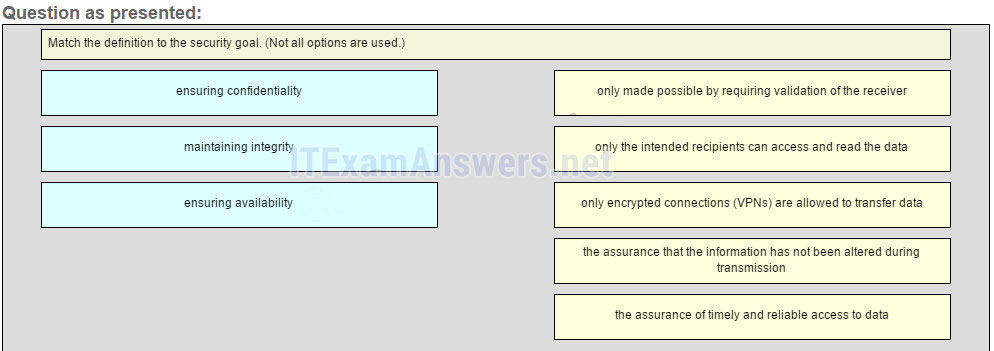
24. Match the definition to the security goal. (Not all options are used.)
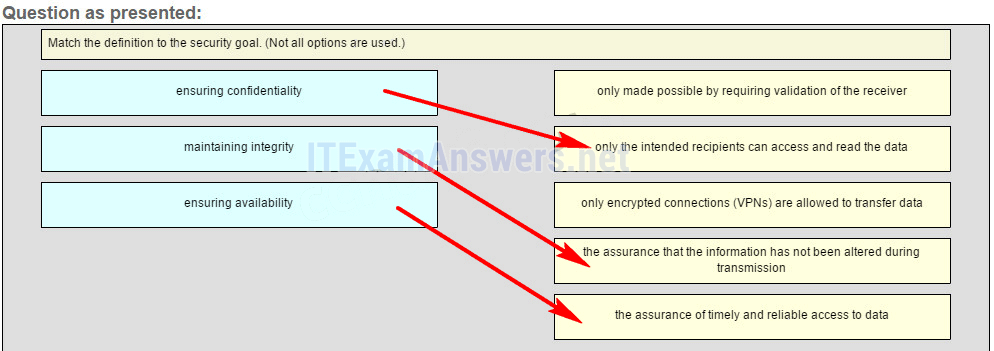
25. What type of network must a home user access in order to do online shopping?
- an intranet
- the Internet
- an extranet
- a local area network
26. What type of network traffic requires QoS?
- on-line purchasing
- video conferencing
- wiki
27. A network administrator is implementing a policy that requires strong, complex passwords. Which data protection goal does this policy support?
- data integrity
- data quality
- data confidentiality
- data redundancy
28. What are two characteristics of a scalable network? (Choose two.)
- easily overloaded with increased traffic
- grows in size without impacting existing users
- is not as reliable as a small network
- suitable for modular devices that allow for expansion
- offers limited number of applications
28. Refer to the exhibit. Which set of devices contains only intermediary devices?
- A, B, D, G
- A, B, E, F
- C, D, G, I
- G, H, I, J
29. Which two statements about the relationship between LANs and WANs are true? (Choose two.)
- Both LANs and WANs connect end devices.
- WANs connect LANs at slower speed bandwidth than LANs connect their internal end devices.
- LANs connect multiple WANs together.
- WANs must be publicly-owned, but LANs can be owned by either public or private entities.
- WANs are typically operated through multiple ISPs, but LANs are typically operated by single organizations or individuals.
30. Which two Internet solutions provide an always-on, high-bandwidth connection to computers on a LAN? (Choose two.) Which two Internet solutions provide an always-on, high-bandwidth connection to computers on a LAN? (Choose two.)
- cellular
- DSL
- satellite
- cable
- dial-up telephone
31. Which description correctly defines a converged network?
- a single network channel capable of delivering multiple communication forms
- a network that allows users to interact directly with each other over multiple channels
- a dedicated network with separate channels for video and voice services
- a network that is limited to exchanging character-based information
32. Which statement describes a network that supports QoS?
- The fewest possible devices are affected by a failure.
- The network should be able to expand to keep up with user demand.
- The network provides predictable levels of service to different types of traffic.
- Data sent over the network is not altered in transmission.
33. What is a characteristic of circuit-switched networks?
- If all circuits are busy, a new call cannot be placed.
- If a circuit fails, the call will be forwarded on a new path.
- Circuit-switched networks can dynamically learn and use redundant circuits.
- A single message can be broken into multiple message blocks that are transmitted through multiple circuits simultaneously.
34. Which expression accurately defines the term congestion?
- a method of limiting the impact of a hardware or software failure on the network
- a measure of the data carrying capacity of the network
- a state where the demand on the network resources exceeds the available capacity
- a set of techniques to manage the utilization of network resources
35. Which tool provides real-time video and audio communication over the Internet so that businesses can conduct corporate meetings with participants from several remote locations?
- wiki
- weblog
- TelePresence
- instant messaging
36. Requiring strong, complex passwords is a practice that supports which network security goal?
- maintaining communication integrity
- ensuring reliability of access
- ensuring data confidentiality
- ensuring redundancy
37. Which three network tools provide the minimum required security protection for home users? (Choose three.)
- an intrusion prevention system
- antivirus software
- antispyware software
- access control lists
- a firewall
- powerline networking
38. Which two Internet solutions provide an always-on, high-bandwidth connection to computers on a LAN? (Choose two.)
- cellular
- DSL
- satellite
- cable
- dial-up telephone
39. What two criteria are used to help select network media? (Choose two.)
- the distance the media can successfully carry a signal
- the environment where the media is to be installed
- the cost of the end devices utilized in the network
- the number of intermediary devices installed in the network
- the types of data that need to be prioritized
40. Fill in the blank.
The acronym byod refers to the trend of end users being able to use their personal devices to access the business network and resources.
41. A college is building a new dormitory on its campus. Workers are digging in the ground to install a new water pipe for the dormitory. A worker accidentally damages a fiber optic cable that connects two of the existing dormitories to the campus data center. Although the cable has been cut, students in the dormitories only experience a very short interruption of network services. What characteristic of the network is shown here?
- quality of service (QoS)
- scalability
- security
- fault tolerance
- integrity
CCNA 1 – ITN Chapter 2 Exam Answers
1. What is the function of the kernel of an operating software?
- It provides a user interface that allows users to request a specific task.
- The kernel links the hardware drivers with the underlying electronics of a computer.
- It is an application that allows the initial configuration of a Cisco device.
- The kernel provisions hardware resources to meet software requirements.
2. A network administrator needs to keep the user ID, password, and session contents private when establishing remote CLI connectivity with a switch to manage it. Which access method should be chosen?
- Telnet
- Console
- AUX
- SSH
3. Which procedure is used to access a Cisco 2960 switch when performing an initial configuration in a secure environment?
- Use Telnet to remotely access the switch through the network.
- Use the console port to locally access the switch from a serial or USB interface of the PC.
- Use Secure Shell to remotely access the switch through the network.
- Use the AUX port to locally access the switch from a serial or USB interface of the PC.
4. Which command or key combination allows a user to return to the previous level in the command hierarchy?
- end
- exit
- Ctrl-Z
- Ctrl-C
5. A router has a valid operating system and a configuration file stored in NVRAM. The configuration file contains an enable secret password but no console password. When the router boots up, which mode will display?
- global configuration mode
- setup mode
- privileged EXEC mode
- user EXEC mode
6. Which two functions are provided to users by the context-sensitive help feature of the Cisco IOS CLI? (Choose two.)
- providing an error message when a wrong command is submitted
- displaying a list of all available commands within the current mode
- allowing the user to complete the remainder of an abbreviated command with the TAB key
- determining which option, keyword, or argument is available for the entered command
- selecting the best command to accomplish a task
7. Which information does the show startup-config command display?
- the IOS image copied into RAM
- the bootstrap program in the ROM
- the contents of the current running configuration file in the RAM
- the contents of the saved configuration file in the NVRAM
8. Why is it important to configure a hostname on a device?
- a Cisco router or switch only begins to operate when its hostname is set
- a hostname must be configured before any other parameters
- to identify the device during remote access (SSH or telnet)
- to allow local access to the device through the console port
9. Which two host names follow the guidelines for naming conventions on Cisco IOS devices? (Choose two.)
- Branch2!
- RM-3-Switch-2A4
- Floor(15)
- HO Floor 17
- SwBranch799
10. How does the service password-encryption command enhance password security on Cisco routers and switches?
- It encrypts passwords as they are sent across the network.
- It encrypts passwords that are stored in router or switch configuration files.
- It requires that a user type encrypted passwords to gain console access to a router or switch.
- It requires encrypted passwords to be used when connecting remotely to a router or switch with Telnet.
11. In your opinion (this has no bearing on your grade), please indicate how enthusiastic you are about the content of this course and the things you’re learning (or have learned):
- Not At All Enthusiastic
- Slightly Enthusiastic
- Enthusiastic
- Very Enthusiastic
- Completely Enthusiastic
12. In your opinion (this has no bearing on your grade), please indicate your interest in this course:
- Not At All Interested
- Slightly Interested
- Interested
- Very Interested
- Completely Interested
13. Refer to the exhibit. A network administrator is configuring the MOTD on switch SW1. What is the purpose of this command?
- to display a message when a user accesses the switch
- to configure switch SW1 so that only the users in the Admin group can telnet into SW1
- to force users of the Admin group to enter a password for authentication
- to configure switch SW1 so that the message will display when a user enters the enable command
14. While trying to solve a network issue, a technician made multiple changes to the current router configuration file. The changes did not solve the problem and were not saved. What action can the technician take to discard the changes and work with the file in NVRAM?
- Issue the reload command without saving the running configuration.
- Delete the vlan.dat file and reboot the device.
- Close and reopen the terminal emulation software.
- Issue the copy startup-config running-config command.
15. What is the function of the kernel of an operating system?
- It provides a user interface that allows users to request a specific task.
- The kernel links the hardware drivers with the underlying electronics of a computer.
- It is an application that allows the initial configuration of a Cisco device.
- The kernel provisions hardware resources to meet software requirements.
16. A router with a valid operating system contains a configuration file stored in NVRAM. The configuration file has an enable secret password but no console password. When the router boots up, which mode will display?
- privileged EXEC mode
- setup mode
- user EXEC mode
- global configuration mode
17. In your opinion (this has no bearing on your grade), please rate your motivation to do well in this course:
- Not At All Motivated
- Slightly Motivated
- Motivated
- Very Motivated
- Completely Motivated
18. Which statement is true about the running configuration file in a Cisco IOS device?
- It affects the operation of the device immediately when modified.
- It is stored in NVRAM.
- It should be deleted using the erase running-config command.
- It is automatically saved when the router reboots.
19. What are two characteristics of RAM on a Cisco device? (Choose two.)
- RAM provides nonvolatile storage.
- The configuration that is actively running on the device is stored in RAM.
- The contents of RAM are lost during a power cycle.
- RAM is a component in Cisco switches but not in Cisco routers.
- RAM is able to store multiple versions of IOS and configuration files.
20. Which interface allows remote management of a Layer 2 switch?
- the AUX interface
- the console port interface
- the switch virtual interface
- the first Ethernet port interface
21. Which interface is the default SVI on a Cisco switch?
- FastEthernet 0/1
- GigabitEthernet 0/1
- VLAN 1
- VLAN 99
22. Why would a Layer 2 switch need an IP address?
- to enable the switch to send broadcast frames to attached PCs
- to enable the switch to function as a default gateway
- to enable the switch to be managed remotely
- to enable the switch to receive frames from attached PCs
23. What command can be used on a Windows PC to see the IP configuration of that computer?
- ping
- ipconfig
- show interfaces
- show ip interface brief
24. A technician is adding a new PC to a LAN. After unpacking the components and making all the connections, the technician starts the PC. After the OS loads, the technician opens a browser, and verifies that the PC can reach the Internet. Why was the PC able to connect to the network with no additional configuration?
- The PC does not require any additional information to function on the network.
- The PC came preconfigured with IP addressing information from the factory.
- The PC was preconfigured to use DHCP.
- The PC used DNS to automatically receive IP addressing information from a server.
- The PC virtual interface is compatible with any network.
25. What is a user trying to determine when issuing a ping 10.1.1.1 command on a PC?
- if the TCP/IP stack is functioning on the PC without putting traffic on the wire
- if there is connectivity with the destination device
- the path that traffic will take to reach the destination
- what type of device is at the destination
26. Refer to the exhibit. A network technician is testing connectivity in a new network. Based on the test results shown in the exhibit, which device does the technician have connectivity with and which device does the technician not have connectivity with? (Choose two.)
- connectivity: switch 2
- connectivity: PC-D
- connectivity: PC-B
- no connectivity: switch 1
- no connectivity: switch 2
- no connectivity: PC-C
27. Refer to the exhibit.
Refer to the exhibit. What three facts can be determined from the viewable output of the show ip interface brief command? (Choose three.)
- Two physical interfaces have been configured.
- The switch can be remotely managed.
- One device is attached to a physical interface.
- Passwords have been configured on the switch.
- Two devices are attached to the switch.
- The default SVI has been configured.
28. An administrator is configuring a switch console port with a password. In what order will the administrator travel through the IOS modes of operation in order to reach the mode in which the configuration commands will be entered? (Not all options are used.)
| first mode | user EXEC mode |
| second mode | privileged EXEC mode |
| third mode | global configuration mode |
| final mode | line configuration mode |
Place the options in the following order:

29. Match the definitions to their respective CLI hot keys and shortcuts. (Not all options are used.)
Question
Place the options in the following order:
completes abbreviated commands and parameters
displays the next screen
scrolls backwards through previously entered commands
– not scored –
provides context-sensitive help
aborts commands such as trace and ping
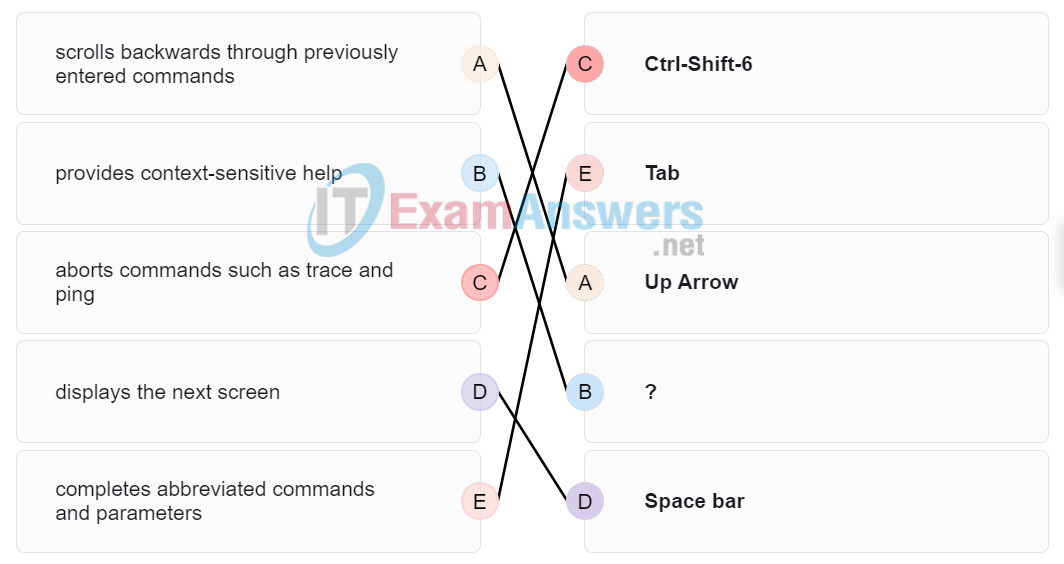
30. A network administrator is planning an IOS upgrade on several of the head office routers and switches. Which three questions must be answered before continuing with the IOS selection and upgrade? (Choose three.)
- Are the devices on the same LAN?
- Do the devices have enough NVRAM to store the IOS image?
- What models of routers and switches require upgrades?
- What ports are installed on the routers and switches?
- Do the routers and switches have enough RAM and flash memory for the proposed IOS versions?
- What features are required for the devices?
31. A router has a valid operating system and a configuration stored in NVRAM. When the router boots up, which mode will display?
- global configuration mode
- setup mode
- ROM monitor mode
- user EXEC mode
32. Which two characters are allowed as part of the hostname of a Cisco device? (Choose two.)
- numbers
- question mark
- space
- tab
- dash
33. What is a result of using the service password-encryption command on a Cisco network device?
- The command encrypts the banner message.
- The command encrypts the enable mode password.
- All passwords in the configuration are not shown in clear text when viewing the configuration.
- A network administrator who later logs into the device will be required to enter an administrator password in order to gain access to the Cisco device.
34. A new network administrator has been asked to enter a banner message on a Cisco device. What is the fastest way a network administrator could test whether the banner is properly configured?
- Reboot the device.
- Enter CTRL-Z at the privileged mode prompt.
- Exit global configuration mode.
- Power cycle the device.
- Exit privileged EXEC mode and press Enter.
35. Passwords can be used to restrict access to all or parts of the Cisco IOS. Select the modes and interfaces that can be protected with passwords. (Choose three.)
- VTY interface
- console interface
- Ethernet interface
- boot IOS mode
- privileged EXEC mode
- router configuration mode
36. What benefit does DHCP provide to a network?
- Hosts always have the same IP address and are therefore always reachable.
- DHCP allows users to refer to locations by a name rather than an IP address.
- Hosts can connect to the network and get an IP address without manual configuration.
- Duplicate addresses cannot occur on a network that issues dynamic addresses using DHCP and has static assignments.
37. What criterion must be followed in the design of an IPv4 addressing scheme for end devices?
- Each IP address must match the address that is assigned to the host by DNS.
- Each IP address must be unique within the local network.
- Each IP address needs to be compatible with the MAC address.
- Each local host should be assigned an IP address with a unique network component.
38. Refer to the exhibit. A switch was configured as shown. A ping to the default gateway was issued, but the ping was not successful. Other switches in the same network can ping this gateway. What is a possible reason for this?
- The VLAN IP address and the default gateway IP address are not in the same network.
- The local DNS server is not functioning correctly.
- The no shutdown command was not issued for VLAN 1.
- The ip default-gateway command has to be issued in the VLAN interface configuration mode.
- The default gateway address must be 192.168.10.1.
39. Match the difinitions to their respective CLI hot keys and shortcuts.
Tab -> Completes abbreviated commands and parameters
Ctrl-R -> returns directly to the privileged EXEC mode
Up Arrow -> scrolls backwards through previously entered commands
Ctrl-Z -> cancels any command currently being entered and returns directly to privileged EXEC mode
Ctrl-C -> Redisplays, on a new line, the command currently being typed
40. Which two features are characteristics of flash memory? (Choose two.)
- Flash receives a copy of the IOS from RAM when a device is powered on.
- Flash provides nonvolatile storage.
- The contents of flash may be overwritten.
- Flash is a component in Cisco switches but not in Cisco routers.
- The contents of flash may be lost during a power cycle.
41. Match the description to the common IOS CLI access method.
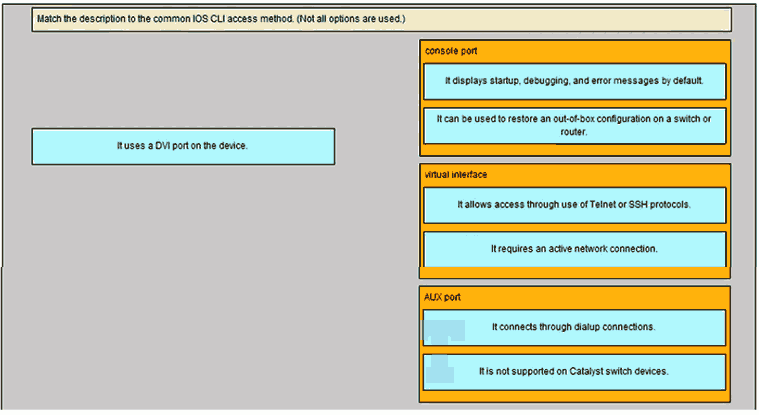
Console port
It displays startup, debugging, and error messages by default.*
It can be used to restore an out-of-box configuration on a switch or router.*
Virtual interface
It allows access throught use of Telnet or SSH protocols.*
It requires an active network connection.*
AUX port
It connects throught dialup connections*
It is not supported on Catalyst switch devices*
41. An employee of a large corporation remotely logs into the company using the appropriate username and password. The employee is attending an important video conference with a customer concerning a large sale. It is important for the video quality to be excellent during the meeting. The employee is unaware that after a successful login, the connection to the company ISP failed. The secondary connection, however, activated within seconds. The disruption was not noticed by the employee or other employees.
42. What three network characteristics are described in this scenario? (Choose three.)
- security
- quality of service
- scalability
- powerline networking
- integrity
- fault tolerance
43. What is the consequence of configuring a router with the ipv6 unicast-routing global configuration command?
- All router interfaces will be automatically activated.
- The IPv6 enabled router interfaces begin sending ICMPv6 Router Advertisement messages.
- Each router interface will generate an IPv6 link-local address.
- It statically creates a global unicast address on this router.
44. What are two ICMPv6 messages that are not present in ICMP for IPv4? (Choose two.)
- Neighbor Solicitation
- Destination Unreachable
- Host Confirmation
- Time Exceeded
- Router Advertisement
- Route Redirection
45. What two pieces of information are displayed in the output of the show ip interface brief command? (Choose two.)
- IP addresses
- interface descriptions
- MAC addresses
- next-hop addresses
- Layer 1 statuses
- speed and duplex settings
46. A client packet is received by a server. The packet has a destination port number of 80. What service is the client requesting?
- DHCP
- SMTP
- DNS
- HTTP
CCNA 1 – ITN Chapter 3 Exam Answers
1. What method can be used by two computers to ensure that packets are not dropped because too much data is being sent too quickly?
- encapsulation
- flow control
- access method
- response timeout
2. What type of communication will send a message to all devices on a local area network?
- broadcast
- multicast
- unicast
- allcast
3. What process is used to place one message inside another message for transfer from the source to the destination?
- access control
- decoding
- encapsulation
- flow control
4. A web client is sending a request for a webpage to a web server. From the perspective of the client, what is the correct order of the protocol stack that is used to prepare the request for transmission?
- HTTP, IP, TCP, Ethernet
- HTTP, TCP, IP, Ethernet
- Ethernet, TCP, IP, HTTP
- Ethernet, IP, TCP, HTTP
5. Which statement is correct about network protocols?
- Network protocols define the type of hardware that is used and how it is mounted in racks.
- They define how messages are exchanged between the source and the destination.
- They all function in the network access layer of TCP/IP.
- They are only required for exchange of messages between devices on remote networks.
6. Which statement is true about the TCP/IP and OSI models?
- The TCP/IP transport layer and OSI Layer 4 provide similar services and functions.
- The TCP/IP network access layer has similar functions to the OSI network layer.
- The OSI Layer 7 and the TCP/IP application layer provide identical functions.
- The first three OSI layers describe general services that are also provided by the TCP/IP internet layer.
7. What is an advantage of using standards to develop and implement protocols?
- A particular protocol can only be implemented by one manufacturer.
- Products from different manufacturers can interoperate successfully.
- Different manufacturers are free to apply different requirements when implementing a protocol.
- Standards provide flexibility for manufacturers to create devices that comply with unique requirements.
8. What three application layer protocols are part of the TCP/IP protocol suite? (Choose three.)
- ARP
- DHCP
- DNS
- FTP
- NAT
- PPP
9. What are proprietary protocols?
- protocols developed by private organizations to operate on any vendor hardware
- protocols that can be freely used by any organization or vendor
- protocols developed by organizations who have control over their definition and operation
- a collection of protocols known as the TCP/IP protocol suite
10. What is an advantage of network devices using open standard protocols?
- Network communications is confined to data transfers between devices from the same vendor.
- A client host and a server running different operating systems can successfully exchange data.
- Internet access can be controlled by a single ISP in each market.
- Competition and innovation are limited to specific types of products.
11. Refer to the exhibit. If Host1 were to transfer a file to the server, what layers of the TCP/IP model would be used?
- only application and Internet layers
- only Internet and network access layers
- only application, Internet, and network access layers
- application, transport, Internet, and network access layers
- only application, transport, network, data link, and physical layers
- application, session, transport, network, data link, and physical layers
12. Which three layers of the OSI model are comparable in function to the application layer of the TCP/IP model? (Choose three.)
- application
- presentation
- session
- transport
- data link
- physical
- network
13. At which layer of the OSI model would a logical address be encapsulated?
- physical layer
- data link layer
- network layer
- transport layer
14. At which layer of the OSI model would a logical address be added during encapsulation?
- physical layer
- data link layer
- network layer
- transport layer
15. Which PDU format is used when bits are received from the network medium by the NIC of a host?
- file
- frame
- packet
- segment
16. Which PDU is processed when a host computer is de-encapsulating a message at the transport layer of the TCP/IP model?
- bits
- frame
- packet
- segment
17. Refer to the exhibit. HostA is attempting to contact ServerB. Which two statements correctly describe the addressing that HostA will generate in the process? (Choose two.)
- A packet with the destination IP address of RouterB.
- A frame with the destination MAC address of SwitchA.
- A packet with the destination IP address of RouterA.
- A frame with the destination MAC address of RouterA.
- A packet with the destination IP address of ServerB.
- A frame with the destination MAC address of ServerB.
18. Which address does a NIC use when deciding whether to accept a frame?
- source IP address
- source MAC address
- destination IP address
- destination MAC address
- source Ethernet address
19. What will happen if the default gateway address is incorrectly configured on a host?
- The host cannot communicate with other hosts in the local network.
- The switch will not forward packets initiated by the host.
- The host will have to use ARP to determine the correct address of the default gateway.
- The host cannot communicate with hosts in other networks.
- A ping from the host to 127.0.0.1 would not be successful.
20. Which characteristic describes the default gateway of a host computer?
- the logical address of the router interface on the same network as the host computer
- the physical address of the switch interface connected to the host computer
- the physical address of the router interface on the same network as the host computer
- the logical address assigned to the switch interface connected to the router
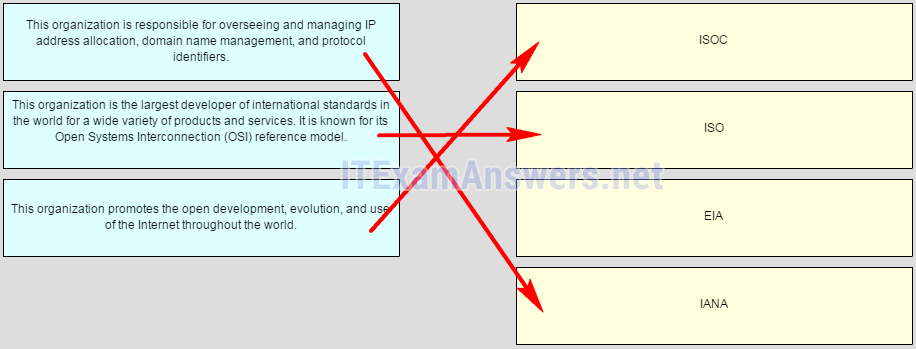
21. Match the description to the organization. (Not all options are used.)
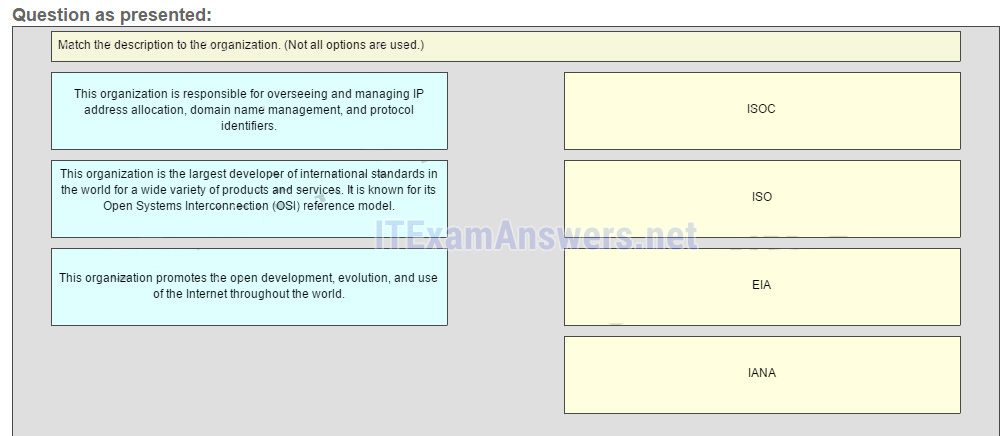
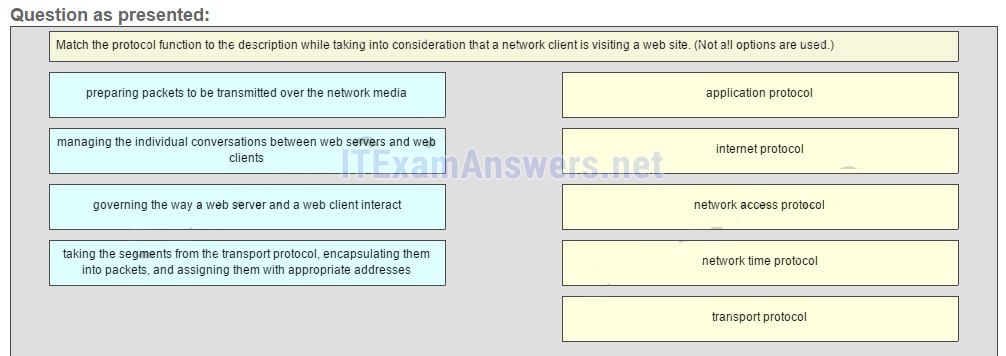
22. Match the protocol function to the description while taking into consideration that a network client is visiting a web site. (Not all options are used.)
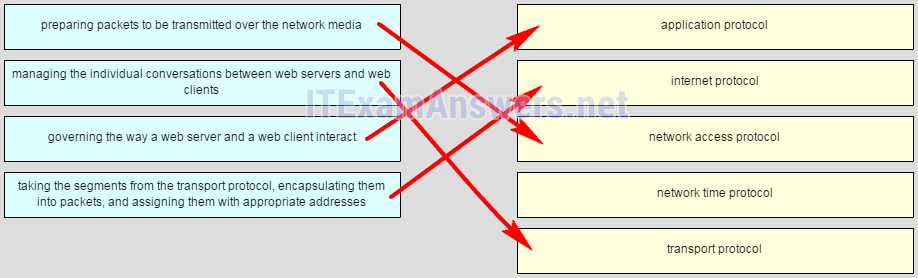
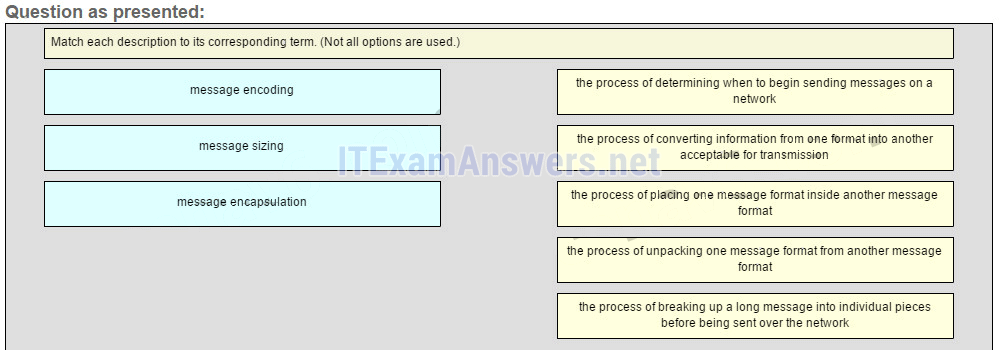
23. Match each description to its corresponding term. (Not all options are used.)
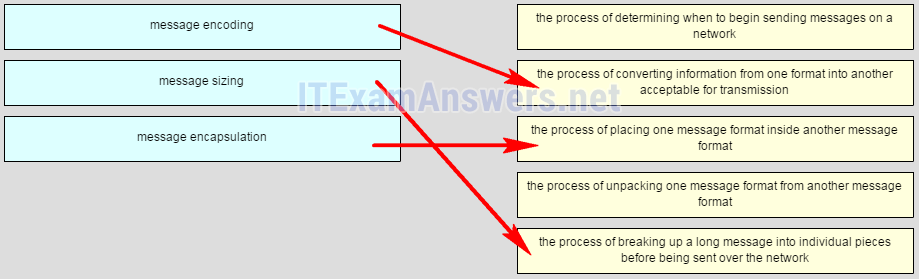
24. A computer in a given network is communicating with a specific group of computers. What type of communication is this?
- broadcast
- multicast
- unicast
- ARP
- HTTP
25. Which protocol is responsible for controlling the size and rate of the HTTP messages exchanged between server and client?
- HTTP
- ARP
- TCP
- DHCP
26. A user is viewing an HTML document located on a web server. What protocol segments the messages and manages the segments in the individual conversation between the web server and the web client?
- DHCP
- TCP
- HTTP
- ARP
27. Which IEEE standard enables a wireless NIC to connect to a wireless AP that is made by a different manufacturer?
- 802.1
- 802.11
- 802.3
- 802.2
28. What is a function of Layer 4 of the OSI model?
- to specify the packet type to be used by the communications
- to apply framing information to the packet, based on the attached media
- to represent data to the user, including encoding and dialog control
- to describe the ordered and reliable delivery of data between source and destination
29. What is a benefit of using a layered model for network communications?
- fostering competition among device and software vendors by enforcing the compatibility of their products
- enhancing network transmission performance by defining targets for each layer
- avoiding possible incompatibility issues by using a common set of developing tools
- simplifying protocol development by limiting every layer to one function
30. What is the general term that is used to describe a piece of data at any layer of a networking model?
- frame
- packet
- protocol data unit
- segment
31. Which statement accurately describes a TCP/IP encapsulation process when a PC is sending data to the network?
- Data is sent from the internet layer to the network access layer.
- Packets are sent from the network access layer to the transport layer.
- Segments are sent from the transport layer to the internet layer.
- Frames are sent from the network access layer to the internet layer.
32. What statement describes the function of the Address Resolution Protocol?
- ARP is used to discover the IP address of any host on a different network.
- ARP is used to discover the IP address of any host on the local network.
- ARP is used to discover the MAC address of any host on a different network.
- ARP is used to discover the MAC address of any host on the local network.
33. Which address provides a unique host address for data communications at the internet layer?
- data-link address
- logical address
- Layer 2 address
- physical address
34. Which protocol is used by a computer to find the MAC address of the default gateway on an Ethernet network?
- ARP
- TCP
- UDP
- DHCP
35. If the default gateway is configured incorrectly on the host, what is the impact on communications?
- The host is unable to communicate on the local network.
- The host can communicate with other hosts on the local network, but is unable to communicate with hosts on remote networks.
- The host can communicate with other hosts on remote networks, but is unable to communicate with hosts on the local network.
- There is no impact on communications.
36. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. Based on the configured network, what IP address would PC1 and PC2 use as their default gateway?
- 192.168.1.2
- 10.1.1.1
- 172.16.1.1
- 192.168.1.1
- 192.168.1.10
37. A user sends an HTTP request to a web server on a remote network. During encapsulation for this request, what information is added to the address field of a frame to indicate the destination?
- the MAC address of the default gateway
- the IP address of the destination host
- the MAC address of the destination host
- the IP address of the default gateway
38. Refer to the exhibit. PC-A and PC-B are both in VLAN 60. PC-A is unable to communicate with PC-B. What is the problem?
- The native VLAN is being pruned from the link.
- The trunk has been configured with the switchport nonegotiate command.
- The native VLAN should be VLAN 60.
- The VLAN that is used by PC-A is not in the list of allowed VLANs on the trunk.
39. Which command is used to remove only VLAN 20 from a switch?
- no switchport access vlan 20
- no vlan 20
- delete vlan.dat
- delete flash:vlan.dat
What characteristic of electricity is expressed in watts?
- the amount of work required to move electrons through a circuit
- the resistance to the flow of current in a circuit
- the amount of electrons flowing through a circuit per second
- the work required to move electrons through a circuit multiplied by the number of electrons flowing through a circuit per second
CCNA 1 – ITN Chapter 4 Exam Answers
1. What are two reasons for physical layer protocols to use frame encoding techniques? (Choose two.)
- to reduce the number of collisions on the media
- to distinguish data bits from control bits
- to provide better media error correction
- to identify where the frame starts and ends
- to increase the media throughput
- to distinguish data from control information
2. What is indicated by the term throughput?
- the guaranteed data transfer rate offered by an ISP
- the capacity of a particular medium to carry data
- the measure of the usable data transferred across the media
- the measure of the bits transferred across the media over a given period of time
- the time it takes for a message to get from sender to receiver
3. A network administrator notices that some newly installed Ethernet cabling is carrying corrupt and distorted data signals. The new cabling was installed in the ceiling close to fluorescent lights and electrical equipment. Which two factors may interfere with the copper cabling and result in signal distortion and data corruption? (Choose two.)
- EMI
- crosstalk
- RFI
- signal attenuation
- extended length of cabling
4. Which characteristic describes crosstalk?
- the distortion of the network signal from fluorescent lighting
- the distortion of the transmitted messages from signals carried in adjacent wires
- the weakening of the network signal over long cable lengths
- the loss of wireless signal over excessive distance from the access point
5. What technique is used with UTP cable to help protect against signal interference from crosstalk?
- twisting the wires together into pairs
- wrapping a foil shield around the wire pairs
- encasing the cables within a flexible plastic sheath
- terminating the cable with special grounded connectors
6. Refer to the exhibit. The PC is connected to the console port of the switch. All the other connections are made through FastEthernet links. Which types of UTP cables can be used to connect the devices?
- 1 – rollover, 2 – crossover, 3 – straight-through
- 1 – rollover, 2 – straight-through, 3 – crossover
- 1 – crossover, 2 – straight-through, 3 – rollover
- 1 – crossover, 2 – rollover, 3 – straight-through
7. Refer to the exhibit. What is wrong with the displayed termination?
- The woven copper braid should not have been removed.
- The wrong type of connector is being used.
- The untwisted length of each wire is too long.
- The wires are too thick for the connector that is used.
8. Which type of connector does a network interface card use?
- DIN
- PS-2
- RJ-11
- RJ-45
9. What is one advantage of using fiber optic cabling rather than copper cabling?
- It is usually cheaper than copper cabling.
- It is able to be installed around sharp bends.
- It is easier to terminate and install than copper cabling.
- It is able to carry signals much farther than copper cabling.
10. Why are two strands of fiber used for a single fiber optic connection?
- The two strands allow the data to travel for longer distances without degrading.
- They prevent crosstalk from causing interference on the connection.
- They increase the speed at which the data can travel.
- They allow for full-duplex connectivity.
11. A network administrator is designing the layout of a new wireless network. Which three areas of concern should be accounted for when building a wireless network? (Choose three.)
- mobility options
- security
- interference
- coverage area
- extensive cabling
- packet collision
12. Which layer of the OSI model is responsible for specifying the encapsulation method used for specific types of media?
- application
- transport
- data link
- physical
13. What are two services performed by the data link layer of the OSI model? (Choose two.)
- It encrypts data packets.
- It determines the path to forward packets.
- It accepts Layer 3 packets and encapsulates them into frames.
- It provides media access control and performs error detection.
- It monitors the Layer 2 communication by building a MAC address table.
14. What is true concerning physical and logical topologies?
- The logical topology is always the same as the physical topology.
- Physical topologies are concerned with how a network transfers frames.
- Physical topologies display the IP addressing scheme of each network.
- Logical topologies refer to how a network transfers data between devices.
15. Which method of data transfer allows information to be sent and received at the same time?
- full duplex
- half duplex
- multiplex
- simplex
16. Which statement describes an extended star topology?
- End devices connect to a central intermediate device, which in turn connects to other central intermediate devices.
- End devices are connected together by a bus and each bus connects to a central intermediate device.
- Each end system is connected to its respective neighbor via an intermediate device.
- All end and intermediate devices are connected in a chain to each other.
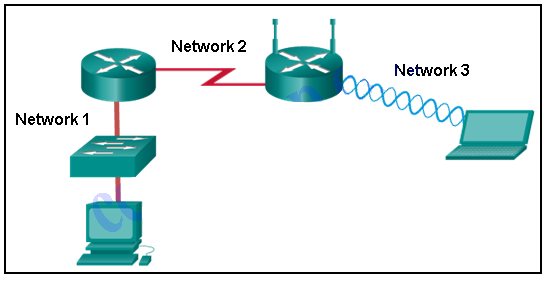
17. Refer to the exhibit. Which statement describes the media access control methods that are used by the networks in the exhibit?
- All three networks use CSMA/CA
- None of the networks require media access control.
- Network 1 uses CSMA/CD and Network 3 uses CSMA/CA.
- Network 1 uses CSMA/CA and Network 2 uses CSMA/CD.
- Network 2 uses CSMA/CA and Network 3 uses CSMA/CD.
18. What is contained in the trailer of a data-link frame?
- logical address
- physical address
- data
- error detection
19. As data travels on the media in a stream of 1s and 0s how does a receiving node identify the beginning and end of a frame?
- The transmitting node inserts start and stop bits into the frame.
- The transmitting node sends a beacon to notify that a data frame is attached.
- The receiving node identifies the beginning of a frame by seeing a physical address.
- The transmitting node sends an out-of-band signal to the receiver about the beginning of the frame.
20. What is a role of the Logical Link Control sublayer?
- to provide data link layer addressing
- to provide access to various Layer 1 network technologies
- to define the media access processes performed by network hardware
- to mark frames to identify the network layer protocol being carried
21. What is the definition of bandwidth?
- the measure of usable data transferred over a given period of time
- the speed at which bits travel on the network
- the measure of the transfer of bits across the media over a given period of time
- the amount of data that can flow from one place to another in a given amount of time
22. What is the function of the CRC value that is found in the FCS field of a frame?
- to verify the integrity of the received frame
- to verify the physical address in the frame
- to verify the logical address in the frame
- to compute the checksum header for the data field in the frame
23. Fill in the blank.
The term bandwidth indicates the capacity of a medium to carry data and it is typically measured in kilobits per second (kb/s) or megabits per second (Mb/s).
24. Fill in the blank.
What acronym is used to reference the data link sublayer that identifies the network layer protocol encapsulated in the frame? LLC
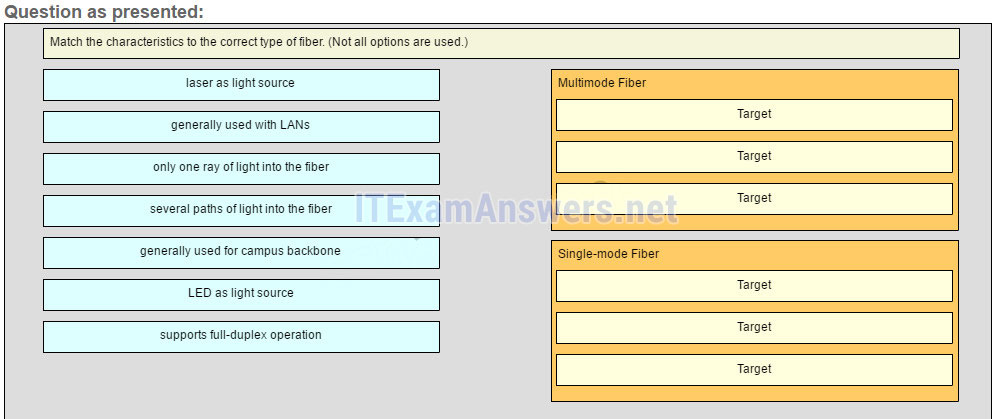
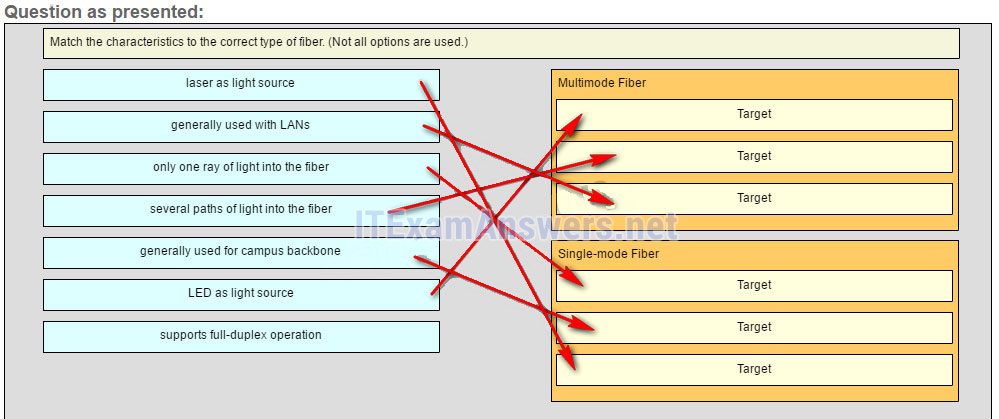
25. Match the characteristics to the correct type of fiber. (Not all options are used.)
26. Fill in the blank.
A physical topology that is a variation or combination of a point-to-point, hub and spoke, or mesh topology is commonly known as a hybrid topology.
27. What are two examples of hybrid topologies? (Choose two.)
- point-to-point
- partial mesh
- extended star
- hub and spoke
- full mesh
28. Which statement describes signaling at the physical layer?
- Sending the signals asynchronously means that they are transmitted without a clock signal.
- In signaling, a 1 always represents voltage and a 0 always represents the absence of voltage.
- Wireless encoding includes sending a series of clicks to delimit the frames.
- Signaling is a method of converting a stream of data into a predefined code
29. The throughput of a FastEthernet network is 80 Mb/s. The traffic overhead for establishing sessions, acknowledgments, and encapsulation is 15 Mb/s for the same time period. What is the goodput for this network?
- 15 Mb/s
- 95 Mb/s
- 55 Mb/s
- 65 Mb/s
- 80 Mb/s
30. How is the magnetic field cancellation effect enhanced in UTP cables?
- by increasing the thickness of the PVC sheath that encases all the wires
- by increasing and varying the number of twists in each wire pair
- by increasing the thickness of the copper wires
- by decreasing the number of wires that are used to carry data
31. Which statement is correct about multimode fiber?
- Multimode fiber cables carry signals from multiple connected sending devices.
- Multimode fiber commonly uses a laser as a light source.
- SC-SC patch cords are used with multimode fiber cables.
- Multimode fiber has a thinner core than single-mode fiber..
32. A network administrator is required to upgrade wireless access to end users in a building. To provide data rates up to 1.3 Gb/s and still be backward compatible with older devices, which wireless standard should be implemented?
- 802.11n
- 802.11ac
- 802.11g
- 802.11b
33. What is one main characteristic of the data link layer?
- It generates the electrical or optical signals that represent the 1 and 0 on the media.
- It converts a stream of data bits into a predefined code.
- It shields the upper layer protocol from being aware of the physical medium to be used in the communication.
- It accepts Layer 3 packets and decides the path by which to forward a frame to a host on a remote network.
34. What are two characteristics of 802.11 wireless networks? (Choose two.)
- They use CSMA/CA technology.
- They use CSMA/CD technology.
- They are collision-free networks.
- Stations can transmit at any time.
- Collisions can exist in the networks.
35. What is the purpose of the FCS field in a frame?
- to obtain the MAC address of the sending node
- to verify the logical address of the sending node
- to compute the CRC header for the data field
- to determine if errors occurred in the transmission and reception
36. Fill in the blank with a number.
10,000,000,000 b/s can also be written as 10 Gb/s.
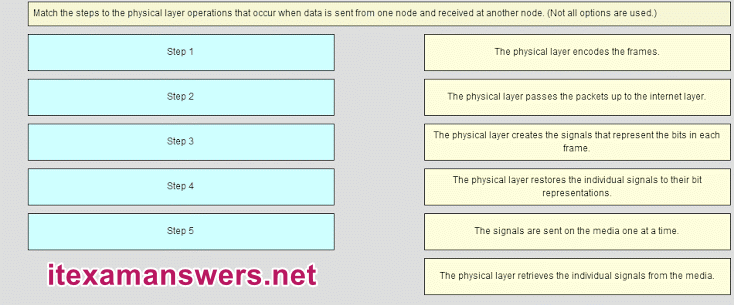
37. Match the steps to the physical layer operations that occur when data is sent from one node and received at another node.
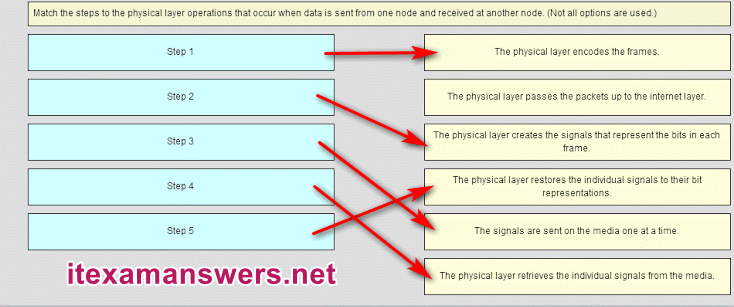
38. Refer to the exhibit.
Which statement describes the media access control methods that are used by the networks in the exhibit?
All three networks use CSMA/CA
- None of the networks require media access control.
- Network 1 uses CSMA/CD and Network 3 uses CSMA/CA.
- Network 1 uses CSMA/CA and Network 2 uses CSMA/CD.
- Network 2 uses CSMA/CA and Network 3 uses CSMA/CD.
CCNA 1 – ITN Chapter 5 Exam Answers
1. What happens to runt frames received by a Cisco Ethernet switch?
- The frame is dropped.
- The frame is returned to the originating network device.
- The frame is broadcast to all other devices on the same network.
- The frame is sent to the default gateway.
2. What are the two sizes (minimum and maximum) of an Ethernet frame? (Choose two.)
- 56 bytes
- 64 bytes
- 128 bytes
- 1024 bytes
- 1518 bytes
3. What statement describes Ethernet?
- It defines the most common LAN type in the world.
- It is the required Layer 1 and 2 standard for Internet communication.
- It defines a standard model used to describe how networking works.
- It connects multiple sites such as routers located in different countries.
4. Which two statements describe features or functions of the logical link control sublayer in Ethernet standards? (Choose two.)
- Logical link control is implemented in software.
- Logical link control is specified in the IEEE 802.3 standard.
- The LLC sublayer adds a header and a trailer to the data.
- The data link layer uses LLC to communicate with the upper layers of the protocol suite.
- The LLC sublayer is responsible for the placement and retrieval of frames on and off the media.
5. What statement describes a characteristic of MAC addresses?
- They must be globally unique.
- They are only routable within the private network.
- They are added as part of a Layer 3 PDU.
- They have a 32-bit binary value.
6. Which statement is true about MAC addresses?
- MAC addresses are implemented by software.
- A NIC only needs a MAC address if connected to a WAN.
- The first three bytes are used by the vendor assigned OUI.
- The ISO is responsible for MAC addresses regulations.
7. Which destination address is used in an ARP request frame?
- 0.0.0.0
- 255.255.255.255
- FFFF.FFFF.FFFF
- 127.0.0.1
- 01-00-5E-00-AA-23
8. What addressing information is recorded by a switch to build its MAC address table?
- the destination Layer 3 address of incoming packets
- the destination Layer 2 address of outgoing frames
- the source Layer 3 address of outgoing packets
- the source Layer 2 address of incoming frames
9. Refer to the exhibit. The exhibit shows a small switched network and the contents of the MAC address table of the switch. PC1 has sent a frame addressed to PC3. What will the switch do with the frame?
- The switch will discard the frame.
- The switch will forward the frame only to port 2.
- The switch will forward the frame to all ports except port 4.
- The switch will forward the frame to all ports.
- The switch will forward the frame only to ports 1 and 3.
10. Which switching method uses the CRC value in a frame?
- cut-through
- fast-forward
- fragment-free
- store-and-forward
11. What is auto-MDIX?
- a type of Cisco switch
- an Ethernet connector type
- a type of port on a Cisco switch
- a feature that detects Ethernet cable type
12. Refer to the exhibit. PC1 issues an ARP request because it needs to send a packet to PC2. In this scenario, what will happen next?
- PC2 will send an ARP reply with its MAC address.
- RT1 will send an ARP reply with its Fa0/0 MAC address.
- RT1 will send an ARP reply with the PC2 MAC address.
- SW1 will send an ARP reply with the PC2 MAC address.
- SW1 will send an ARP reply with its Fa0/1 MAC address.
13. What is the aim of an ARP spoofing attack?
- to associate IP addresses to the wrong MAC address
- to overwhelm network hosts with ARP requests
- to flood the network with ARP reply broadcasts
- to fill switch MAC address tables with bogus addresses
14. What is a characteristic of port-based memory buffering?
- Frames in the memory buffer are dynamically linked to destination ports.
- All frames are stored in a common memory buffer.
- Frames are buffered in queues linked to specific ports.
- All ports on a switch share a single memory buffer.
15. What is the minimum Ethernet frame size that will not be discarded by the receiver as a runt frame?
- 64 bytes
- 512 bytes
- 1024 bytes
- 1500 bytes
16. What are two potential network problems that can result from ARP operation? (Choose two.)
- Manually configuring static ARP associations could facilitate ARP poisoning or MAC address spoofing.
- On large networks with low bandwidth, multiple ARP broadcasts could cause data communication delays.
- Network attackers could manipulate MAC address and IP address mappings in ARP messages with the intent of intercepting network traffic.
- Large numbers of ARP request broadcasts could cause the host MAC address table to overflow and prevent the host from communicating on the network.
- Multiple ARP replies result in the switch MAC address table containing entries that match the MAC addresses of hosts that are connected to the relevant switch port.
17. Fill in the blank.
A collision fragment, also known as a RUNT frame, is a frame of fewer than 64 bytes in length.
18. Fill in the blank.
On a Cisco switch, port-based memory buffering is used to buffer frames in queues linked to specific incoming and outgoing ports.
19. Fill in the blank.
ARP spoofing is a technique that is used to send fake ARP messages to other hosts in the LAN. The aim is to associate IP addresses to the wrong MAC addresses.
20. Which statement describes the treatment of ARP requests on the local link?
- They must be forwarded by all routers on the local network.
- They are received and processed by every device on the local network.
- They are dropped by all switches on the local network.
- They are received and processed only by the target device.
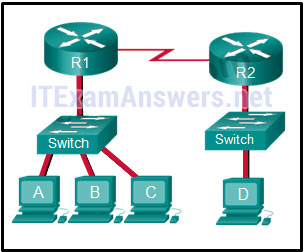
21. Refer to the exhibit. The switches are in their default configuration. Host A needs to communicate with host D, but host A does not have the MAC address for its default gateway. Which network hosts will receive the ARP request sent by host A?
- only host D
- only router R1
- only hosts A, B, and C
- only hosts A, B, C, and D
- only hosts B and C
- only hosts B, C, and router R1
22. Refer to the exhibit. A switch with a default configuration connects four hosts. The ARP table for host A is shown. What happens when host A wants to send an IP packet to host D?
- Host A sends an ARP request to the MAC address of host D.
- Host D sends an ARP request to host A.
- Host A sends out the packet to the switch. The switch sends the packet only to the host D, which in turn responds.
- Host A sends out a broadcast of FF:FF:FF:FF:FF:FF. Every other host connected to the switch receives the broadcast and host D responds with its MAC address.
23. True or False?
When a device is sending data to another device on a remote network, the Ethernet frame is sent to the MAC address of the default gateway.
- true
- false
24. The ARP table in a switch maps which two types of address together?
- Layer 3 address to a Layer 2 address
- Layer 3 address to a Layer 4 address
- Layer 4 address to a Layer 2 address
- Layer 2 address to a Layer 4 address
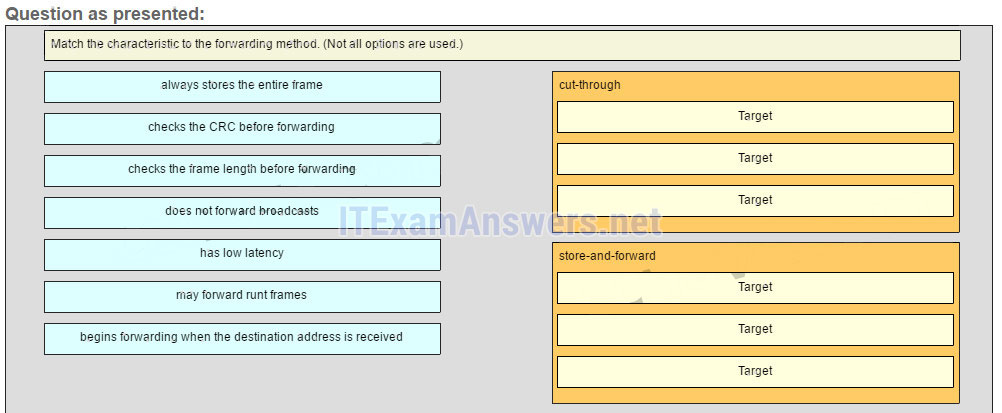
25. Match the characteristic to the forwarding method. (Not all options are used.)
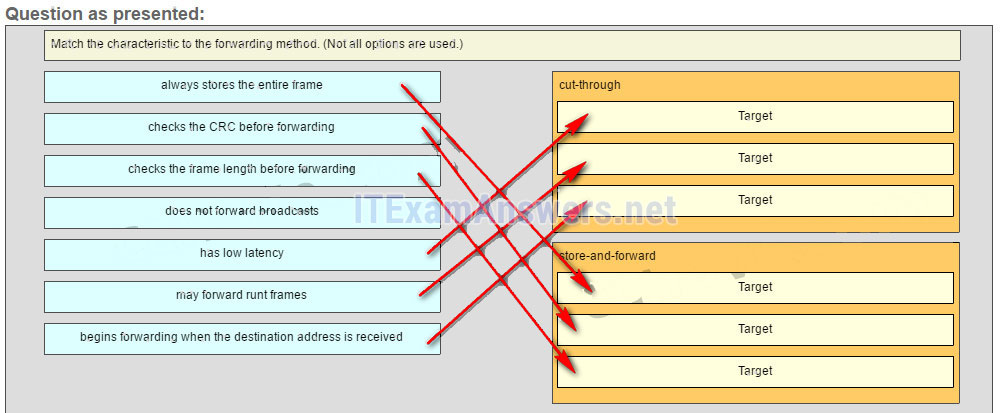
26. What is a characteristic of a contention-based access method?
- It processes more overhead than the controlled access methods do.
- It has mechanisms to track the turns to access the media.
- It is a nondeterministic method.
- It scales very well under heavy media use.
27. What is the purpose of the preamble in an Ethernet frame?
- is used as a padding for data
- is used for timing synchronization
- is used to identify the source address
- is used to identify the destination address
28. What is the Layer 2 multicast MAC address that corresponds to the Layer 3 IPv4 multicast address 224.139.34.56?
- 00-00-00-0B-22-38
- 01-00-5E-0B-22-38
- 01-5E-00-0B-22-38
- FE-80-00-0B-22-38
- FF-FF-FF-0B-22-38
29. Which two statements are correct about MAC and IP addresses during data transmission if NAT is not involved? (Choose two.)
- A packet that has crossed four routers has changed the destination IP address four times.
- Destination MAC addresses will never change in a frame that goes across seven routers.
- Destination and source MAC addresses have local significance and change every time a frame goes from one LAN to another.
- Destination IP addresses in a packet header remain constant along the entire path to a target host.
- Every time a frame is encapsulated with a new destination MAC address, a new destination IP address is needed.
30. What are two features of ARP? (Choose two.)
- If a host is ready to send a packet to a local destination device and it has the IP address but not the MAC address of the destination, it generates an ARP broadcast.
- An ARP request is sent to all devices on the Ethernet LAN and contains the IP address of the destination host and its multicast MAC address.
- When a host is encapsulating a packet into a frame, it refers to the MAC address table to determine the mapping of IP addresses to MAC addresses.
- If no device responds to the ARP request, then the originating node will broadcast the data packet to all devices on the network segment.
- If a device receiving an ARP request has the destination IPv4 address, it responds with an ARP reply.
31. A host is trying to send a packet to a device on a remote LAN segment, but there are currently no mappings in its ARP cache. How will the device obtain a destination MAC address?
- It will send an ARP request for the MAC address of the destination device.
- It will send an ARP request for the MAC address of the default gateway.
- It will send the frame and use its own MAC address as the destination.
- It will send the frame with a broadcast MAC address.
- It will send a request to the DNS server for the destination MAC address.
32. A network administrator is connecting two modern switches using a straight-through cable. The switches are new and have never been configured. Which three statements are correct about the final result of the connection? (Choose three.)
- The link between the switches will work at the fastest speed that is supported by both switches.
- The link between switches will work as full-duplex.
- If both switches support different speeds, they will each work at their own fastest speed.
- The auto-MDIX feature will configure the interfaces eliminating the need for a crossover cable.
- The connection will not be possible unless the administrator changes the cable to a crossover cable.
- The duplex capability has to be manually configured because it cannot be negotiated.
33. A Layer 2 switch is used to switch incoming frames from a 1000BASE-T port to a port connected to a 100Base-T network. Which method of memory buffering would work best for this task?
- port-based buffering
- level 1 cache buffering
- shared memory buffering
- fixed configuration buffering
34. When would a switch record multiple entries for a single switch port in its MAC address table?
- when a router is connected to the switch port
- when multiple ARP broadcasts have been forwarded
- when another switch is connected to the switch port
- when the switch is configured for Layer 3 switching
35. Which two statements describe a fixed configuration Ethernet switch? (Choose two.)
- The switch cannot be configured with multiple VLANs.
- An SVI cannot be configured on the switch.
- A fixed configuration switch may be stackable.
- The number of ports on the switch cannot be increased.
- The port density of the switch is determined by the Cisco IOS.
36. How does adding an Ethernet line card affect the form factor of a switch?
- by increasing the back plane switching speed
- by expanding the port density
- by making the switch stackable
- by expanding the NVRAM capacity
37. Which address or combination of addresses does a Layer 3 switch use to make forwarding decisions?
- IP address only
- port address only
- MAC address only
- MAC and port addresses
- MAC and IP addresses
38. What statement illustrates a drawback of the CSMA/CD access method?
- Deterministic media access protocols slow network performance.
- It is more complex than non-deterministic protocols.
- Collisions can decrease network performance.
- CSMA/CD LAN technologies are only available at slower speeds than other LAN technologies.
39. Open the PT Activity. Perform the tasks in the activity instruction and then answer the question.
What destination address will PC1 include in the destination address field of the Ethernet frame that it sends to PC2?
- 192.168.0.17
- 192.168.0.34
- 0030.a3e5.0401
- 00e0.b0be.8014
- 0007.ec35.a5c6
40. Which address or combination of addresses does a Layer 3 switch use to make forwarding decisions?
- MAC and IP addresses
- MAC address only
- MAC and port addresses
- port address only
- IP address only
41. Launch PT. Hide and Save PT
Open the PT Activity. Perform the tasks in the activity instruction and then answer the question. What destination address will PC1 include in the destination address field of the Ethernet frame that it sends to PC2?
- 00e0.b0be.8014
- 0030.a3e5.0401
- 192.168.0.34
- 192.168.0.17
- 0007.ec35.a5c6
42. How does adding an Ethernet line card affect the form factor of a switch?
- by increasing the back plane switching speed
- by expanding the port density
- by expanding the NVRAM capacity
- by making the switch stackable
43. What statement illustrates a drawback of the CSMA/CD access method?
- Collisions can decrease network performance.
- Deterministic media access protocols slow network performance.
- CSMA/CD LAN technologies are only available at slower speeds than other LAN technologies.
- It is more complex than non-deterministic protocols.
44. What is the administrator configuring?
- a Cisco Express Forwarding instance
- a routed port
- a trunk interface
- a switched virtual interface
45. The binary number 0000 1010 can be expressed as “A” in hexadecimal.
Match the seven fields of an Ethernet frame to their respective contents. (Not all options are used.)
CCNA 1 – ITN Chapter 6 Exam Answers
1. Which characteristic of the network layer in the OSI model allows carrying packets for multiple types of communications among many hosts?
- the de-encapsulation of headers from lower layers
- the selection of paths for and direct packets toward the destination
- the ability to operate without regard to the data that is carried in each packet
- the ability to manage the data transport between processes running on hosts
2. What are two characteristics of IP? (Choose two.)
- does not require a dedicated end-to-end connection
- operates independently of the network media
- retransmits packets if errors occur
- re-assembles out of order packets into the correct order at the receiver end
- guarantees delivery of packets
3. When a connectionless protocol is in use at a lower layer of the OSI model, how is missing data detected and retransmitted if necessary?
- Connectionless acknowledgements are used to request retransmission.
- Upper-layer connection-oriented protocols keep track of the data received and can request retransmission from the upper-level protocols on the sending host.
- Network layer IP protocols manage the communication sessions if connection-oriented transport services are not available.
- The best-effort delivery process guarantees that all packets that are sent are received.
4. Which field in the IPv4 header is used to prevent a packet from traversing a network endlessly?
- Time-to-Live
- Sequence Number
- Acknowledgment Number
- Differentiated Services
5. What IPv4 header field identifies the upper layer protocol carried in the packet?
- Protocol
- Identification
- Version
- Differentiated Services
6. What is one advantage that the IPv6 simplified header offers over IPv4?
- smaller-sized header
- little requirement for processing checksums
- smaller-sized source and destination IP addresses
- efficient packet handling
7. Refer to the exhibit. Which route from the PC1 routing table will be used to reach PC2?
- The graphic contains a table that has five columns. The column headings and values are as follows. The column one heading is Network Destination and the value is 192.168.10.0. The column two heading is Netmask and the value is 255.255.255.0. The column three heading is Gateway and the value is On-link. The column four heading is Interface and the value is 192.168.10.10. The column five heading is Metric and the value is 281.
- The graphic contains a table that has five columns. The column headings and values are as follows. The column one heading is Network Destination and the value is 192.168.10.10. The column two heading is Netmask and the value is 255.255.255.255. The column three heading is Gateway and the value is On-link. The column four heading is Interface and the value is 192.168.10.10. The column five heading is Metric and the value is 281.
- The graphic contains a table that has five columns. The column headings and values are as follows. The column one heading is Network Destination and the value is 127.0.0.1. The column two heading is Netmask and the value is 255.255.255.255. The column three heading is Gateway and the value is On-link. The column four heading is Interface and the value is 127.0.0.1. The column five heading is Metric and the value is 306.
- The graphic contains a table that has five columns. The column headings and values are as follows. The column one heading is Network Destination and the value is 0.0.0.0. The column two heading is Netmask and the value is 0.0.0.0. The column three heading is Gateway and the value is 192.168.10.1. The column four heading is Interface and the value is 192.168.10.10. The column five heading is Metric and the value is 25.
8. Refer to the exhibit. R1 receives a packet destined for the IP address 192.168.2.10. Out which interface will R1 forward the packet?
- FastEthernet0/0
- FastEthernet0/1
- Serial0/0/0
- Serial0/0/1
9. What type of route is indicated by the code C in an IPv4 routing table on a Cisco router?
- static route
- default route
- directly connected route
- dynamic route that is learned through EIGRP
10. What routing table entry has a next hop address associated with a destination network?
- directly-connected routes
- local routes
- remote routes
- C and L source routes
11. Which statement describes a hardware feature of a Cisco 1941 router that has the default hardware configuration?
- It does not have an AUX port.
- It has three FastEthernet interfaces for LAN access.
- It has two types of ports that can be used to access the console.
- It does not require a CPU because it relies on Compact Flash to run the IOS.
12. Following default settings, what is the next step in the router boot sequence after the IOS loads from flash?
- Perform the POST routine.
- Locate and load the startup-config file from NVRAM.
- Load the bootstrap program from ROM.
- Load the running-config file from RAM.
13. What are two types of router interfaces? (Choose two.)
- SVI
- LAN
- DHCP
- Telnet
- WAN
14. Which two pieces of information are in the RAM of a Cisco router during normal operation? (Choose two.)
- Cisco IOS
- backup IOS file
- IP routing table
- basic diagnostic software
- startup configuration file
15. A router boots and enters setup mode. What is the reason for this?
- The IOS image is corrupt.
- Cisco IOS is missing from flash memory.
- The configuration file is missing from NVRAM.
- The POST process has detected hardware failure.
16. What is the purpose of the startup configuration file on a Cisco router?
- to facilitate the basic operation of the hardware components of a device
- to contain the commands that are used to initially configure a router on startup
- to contain the configuration commands that the router IOS is currently using
- to provide a limited backup version of the IOS, in case the router cannot load the full featured IOS
17. Which three commands are used to set up secure access to a router through a connection to the console interface? (Choose three.)
- interface fastethernet 0/0
- line vty 0 4
- line console 0
- enable secret cisco
- login
- password cisco
18. Which characteristic describes an IPv6 enhancement over IPv4?
- IPv6 addresses are based on 128-bit flat addressing as opposed to IPv4 which is based on 32-bit hierarchical addressing.
- The IPv6 header is simpler than the IPv4 header is, which improves packet handling.
- Both IPv4 and IPv6 support authentication, but only IPv6 supports privacy capabilities.
- The IPv6 address space is four times bigger than the IPv4 address space.
19. Open the PT Activity. The enable password on all devices is cisco.
Perform the tasks in the activity instructions and then answer the question.
For what reason is the failure occurring?
- PC1 has an incorrect default gateway configured.
- SW1 does not have a default gateway configured.
- The IP address of SW1 is configured in a wrong subnet.
- PC2 has an incorrect default gateway configured.
20. Match the command with the device mode at which the command is entered. (Not all options are used.)
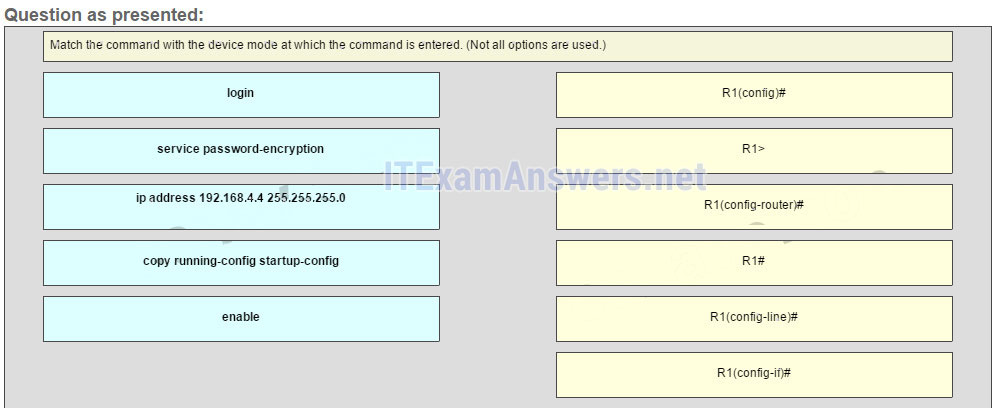
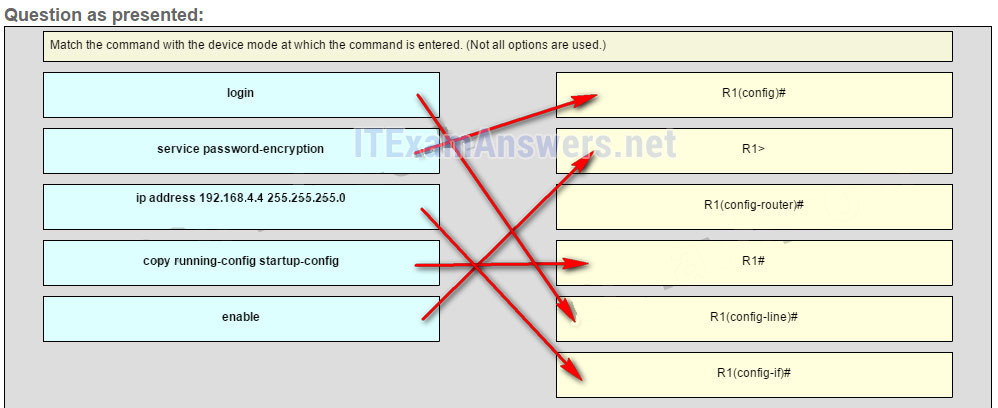
21. When connectionless protocols are implemented at the lower layers of the OSI model, what are usually used to acknowledge the data receipt and request the retransmission of missing data?
- connectionless acknowledgements
- upper-layer connection-oriented protocols
- Network layer IP protocols
- Transport layer UDP protocols
22. Which IPv4 header field is responsible for defining the priority of the packet?
- flow label
- flags
- differentiated services
- traffic class
23. Why is NAT not needed in IPv6?
- Because IPv6 has integrated security, there is no need to hide the IPv6 addresses of internal networks.?
- Any host or user can get a public IPv6 network address because the number of available IPv6 addresses is extremely large.
- The problems that are induced by NAT applications are solved because the IPv6 header improves packet handling by intermediate routers.?
- The end-to-end connectivity problems that are caused by NAT are solved because the number of routes increases with the number of nodes that are connected to the Internet.
24. What is a service provided by the Flow Label field of the IPv6 header?
- It limits the lifetime of a packet.
- It identifies the total length of the IPv6 packet.
- It classifies packets for traffic congestion control.
- It informs network devices to maintain the same path for real-time application packets.
25. How do hosts ensure that their packets are directed to the correct network destination?
- They have to keep their own local routing table that contains a route to the loopback interface, a local network route, and a remote default route.?
- They always direct their packets to the default gateway, which will be responsible for the packet delivery.
- They search in their own local routing table for a route to the network destination address and pass this information to the default gateway.
- They send a query packet to the default gateway asking for the best route.
26. Which two commands can be used on a Windows host to display the routing table? (Choose two.)
- netstat -s
- route print
- show ip route
- netstat -r
- tracert
27. During the process of forwarding traffic, what will the router do immediately after matching the destination IP address to a network on a directly connected routing table entry?
- discard the traffic after consulting the route table
- look up the next-hop address for the packet
- switch the packet to the directly connected interface
- analyze the destination IP address
28. A technician is configuring a router that is actively running on the network. Suddenly, power to the router is lost. If the technician has not saved the configuration, which two types of information will be lost? (Choose two.)
- Cisco IOS image file
- routing table
- bootstrap file
- ARP cache
- startup configuration
29. Which two interfaces will allow access via the VTY lines to configure the router? (Choose two.)
- aux interfaces
- LAN interfaces
- WAN interfaces
- console interfaces
- USB interfaces
30. Which two files, if found, are copied into RAM as a router with the default configuration register setting boots up? (Choose two.)
- running configuration
- IOS image file
- startup configuration
- POST diagnostics
31. When would the Cisco IOS image held in ROM be used to boot the router?
- during a file transfer operation
- during a normal boot process
- when the full IOS cannot be found
- when the running configuration directs the router to do this
32. After troubleshooting a router, the network administrator wants to save the router configuration so that it will be used automatically the next time that the router reboots. What command should be issued?
- copy running-config flash
- copy startup-config flash
- copy running-config startup-config
- reload
- copy startup-config running-config
33. Which three commands are used to set up a password for a person who attaches a cable to a new router so that an initial configuration can be performed? (Choose three.)
- interface fastethernet 0/0
- line vty 0 4
- line console 0
- enable secret cisco
- login
- password cisco
34. Which statement about router interfaces is true?
- Router LAN interfaces are not activated by default, but router WAN interfaces are.
- Once the no shutdown command is given, a router interface is active and operational.
- Commands that apply an IP address and subnet mask to an interface are entered in global configuration mode.
- A configured and activated router interface must be connected to another device in order to operate.
35. Which command displays a summary chart of all router interfaces, their IP addresses, and their current operational status?
- show ip route
- show version
- show interfaces
- show ip interface brief
36. A technician is manually configuring a computer with the necessary IP parameters to communicate over the corporate network. The computer already has an IP address, a subnet mask, and a DNS server. What else has to be configured for Internet access?
- the WINS server address
- the default gateway address
- the MAC address
- the domain name of the organization
37. A computer has to send a packet to a destination host in the same LAN. How will the packet be sent?
- The packet will be sent to the default gateway first, and then, depending on the response from the gateway, it may be sent to the destination host.
- The packet will be sent directly to the destination host.
- The packet will first be sent to the default gateway, and then from the default gateway it will be sent directly to the destination host.
- The packet will be sent only to the default gateway.
38. Refer to the exhibit. Fill in the blank.
A packet leaving PC-1 has to traverse 3 hops to reach PC-4.?
39. Fill in the blank. In a router, ROM is the nonvolatile memory where the diagnostic software, the bootup instructions, and a limited IOS are stored.
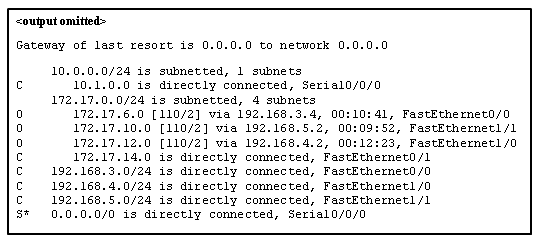
40. Refer to the exhibit. Match the packets with their destination IP address to the exiting interfaces on the router. (Not all targets are used.)
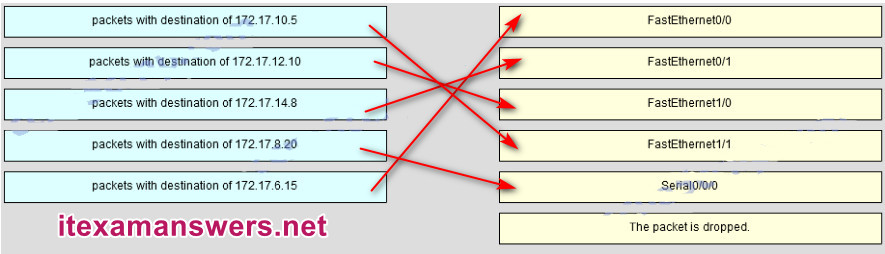
41. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question or complete the task. Does the router have enough RAM and flash memory to support the new IOS?
- The router has enough RAM and flash memory for the IOS upgrade.
- The router has enough RAM, but needs more flash memory for the IOS upgrade.
- The router has enough flash memory, but needs more RAM for the IOS upgrade.
- The router needs more RAM and more flash memory for the IOS upgrade.
42. Match the configuration mode with the command that is available in that mode. (Not all options are used.)
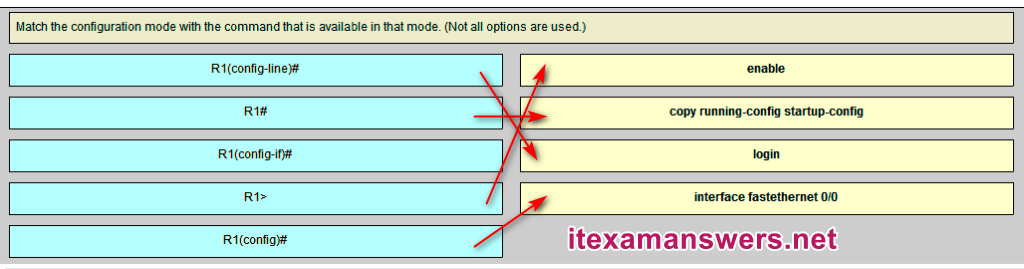
43. Match field names to the IP header where they would be found. (Not all options are used)
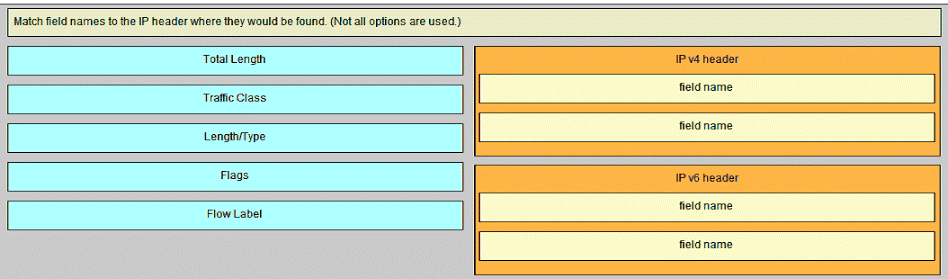
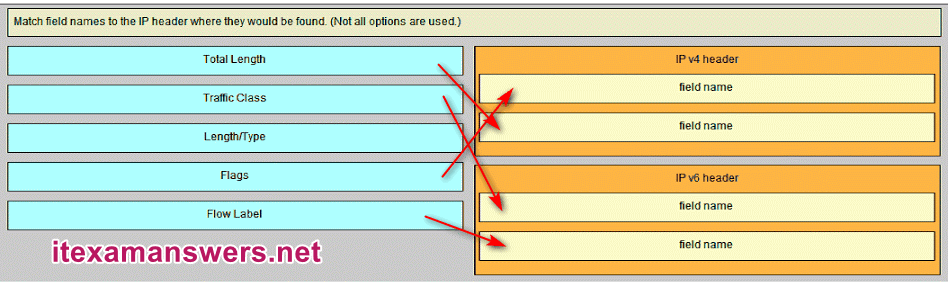
44. Which type of static route that is configured on a router uses only the exit interface?
- fully specified static route
- default static route
- directly connected static route
- recursive static route
CCNA 1 – ITN Chapter 7 Exam Answers
1. How many bits are in an IPv4 address?
- 32
- 64
- 128
- 256
2. Which two parts are components of an IPv4 address? (Choose two.)
- subnet portion
- network portion
- logical portion
- host portion
- physical portion
- broadcast portion
3. What does the IP address 172.17.4.250/24 represent?
- network address
- multicast address
- host address
- broadcast address
4. What is the purpose of the subnet mask in conjunction with an IP address?
- to uniquely identify a host on a network
- to identify whether the address is public or private
- to determine the subnet to which the host belongs
- to mask the IP address to outsiders
5. What subnet mask is represented by the slash notation /20?
- 255.255.255.248
- 255.255.224.0
- 255.255.240.0
- 255.255.255.0
- 255.255.255.192
6. A message is sent to all hosts on a remote network. Which type of message is it?
- limited broadcast
- multicast
- directed broadcast
- unicast
7. What are three characteristics of multicast transmission? (Choose three.)
- The source address of a multicast transmission is in the range of 224.0.0.0 to 224.0.0.255.
- A single packet can be sent to a group of hosts.
- Multicast transmission can be used by routers to exchange routing information.
- The range of 224.0.0.0 to 224.0.0.255 is reserved to reach multicast groups on a local network.
- Computers use multicast transmission to request IPv4 addresses.
- Multicast messages map lower layer addresses to upper layer addresses.
8. Which three IP addresses are private ? (Choose three.)
- 10.1.1.1
- 172.32.5.2
- 192.167.10.10
- 172.16.4.4
- 192.168.5.5
- 224.6.6.6
9. Which two IPv4 to IPv6 transition techniques manage the interconnection of IPv6 domains? (Choose two.)
- trunking
- dual stack
- encapsulation
- tunneling
- multiplexing
10. Which of these addresses is the shortest abbreviation for the IP address:
3FFE:1044:0000:0000:00AB:0000:0000:0057?
- 3FFE:1044::AB::57
- 3FFE:1044::00AB::0057
- 3FFE:1044:0:0:AB::57
- 3FFE:1044:0:0:00AB::0057
- 3FFE:1044:0000:0000:00AB::57
- 3FFE:1044:0000:0000:00AB::0057
11. What type of address is automatically assigned to an interface when IPv6 is enabled on that interface?
- global unicast
- link-local
- loopback
- unique local
12. What are two types of IPv6 unicast addresses? (Choose two.)
- multicast
- loopback
- link-local
- anycast
- broadcast
13. What are three parts of an IPv6 global unicast address? (Choose three.)
- an interface ID that is used to identify the local network for a particular host
- a global routing prefix that is used to identify the network portion of the address that has been provided by an ISP
- a subnet ID that is used to identify networks inside of the local enterprise site
- a global routing prefix that is used to identify the portion of the network address provided by a local administrator
- an interface ID that is used to identify the local host on the network
14. An administrator wants to configure hosts to automatically assign IPv6 addresses to themselves by the use of Router Advertisement messages, but also to obtain the DNS server address from a DHCPv6 server. Which address assignment method should be configured?
- SLAAC
- stateless DHCPv6
- stateful DHCPv6
- RA and EUI-64
15. Which protocol supports Stateless Address Autoconfiguration (SLAAC) for dynamic assignment of IPv6 addresses to a host?
- ARPv6
- DHCPv6
- ICMPv6
- UDP
16. Which two things can be determined by using the ping command? (Choose two.)
- the number of routers between the source and destination device
- the IP address of the router nearest the destination device
- the average time it takes a packet to reach the destination and for the response to return to the source
- the destination device is reachable through the network
- the average time it takes each router in the path between source and destination to respond
17. What is the purpose of ICMP messages?
- to inform routers about network topology changes
- to ensure the delivery of an IP packet
- to provide feedback of IP packet transmissions
- to monitor the process of a domain name to IP address resolution
18. What is indicated by a successful ping to the ::1 IPv6 address?
- The host is cabled properly.
- The default gateway address is correctly configured.
- All hosts on the local link are available.
- The link-local address is correctly configured.
- IP is properly installed on the host.
19. A user is executing a tracert to a remote device. At what point would a router, which is in the path to the destination device, stop forwarding the packet?
- when the router receives an ICMP Time Exceeded message
- when the RTT value reaches zero
- when the host responds with an ICMP Echo Reply message
- when the value in the TTL field reaches zero
- when the values of both the Echo Request and Echo Reply messages reach zero
20. What is the binary equivalent of the decimal number 232?
- 11101000
- 11000110
- 10011000
- 11110010
21. What is the decimal equivalent of the binary number 10010101?
- 149
- 157
- 168
- 192
22. What field content is used by ICMPv6 to determine that a packet has expired?
- TTL field
- CRC field
- Hop Limit field
- Time Exceeded field
23. Fill in the blank.
The decimal equivalent of the binary number 10010101 is 149
24. Fill in the blank.
The binary equivalent of the decimal number 232 is 11101000
25. Fill in the blank.
What is the decimal equivalent of the hex number 0x3F? 63
26. Match each description with an appropriate IP address. (Not all options are used.)
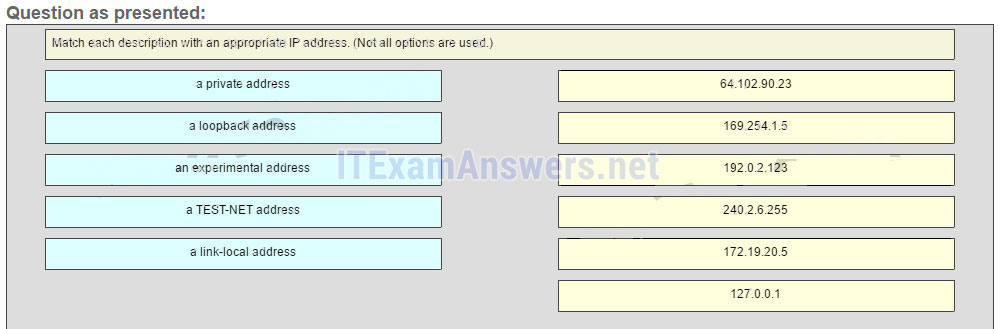
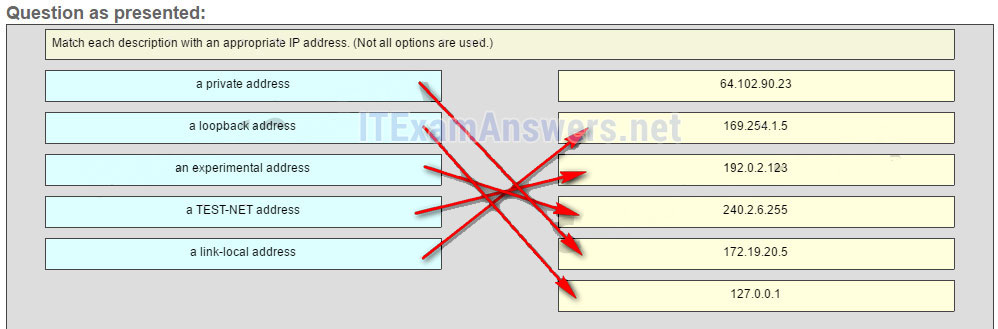
27. What is a socket?
- the combination of the source and destination IP address and source and destination Ethernet address
- the combination of a source IP address and port number or a destination IP address and port number
- the combination of the source and destination sequence and acknowledgment numbers
- the combination of the source and destination sequence numbers and port numbers
28. A host device needs to send a large video file across the network while providing data communication to other users. Which feature will allow different communication streams to occur at the same time, without having a single data stream using all available bandwidth?
- window size
- multiplexing
- port numbers
- acknowledgments
29. A host device sends a data packet to a web server via the HTTP protocol. What is used by the transport layer to pass the data stream to the proper application on the server?
- sequence number
- acknowledgment
- source port number
- destination port number
30. What is a beneficial feature of the UDP transport protocol?
- acknowledgment of received data
- fewer delays in transmission
- tracking of data segments using sequence numbers
- the ability to retransmit lost data
31. Which scenario describes a function provided by the transport layer?
- A student is using a classroom VoIP phone to call home. The unique identifier burned into the phone is a transport layer address used to contact another network device on the same network.
- A student is playing a short web-based movie with sound. The movie and sound are encoded within the transport layer header.
- A student has two web browser windows open in order to access two web sites. The transport layer ensures the correct web page is delivered to the correct browser window.
- A corporate worker is accessing a web server located on a corporate network. The transport layer formats the screen so the web page appears properly no matter what device is being used to view the web site.
32. What is the complete range of TCP and UDP well-known ports?
- 0 to 255
- 0 to 1023
- 256 – 1023
- 1024 – 49151
33. What does a client application select for a TCP or UDP source port number?
- a random value in the well-known port range
- a random value in the range of the registered ports
- a predefined value in the well-known port range
- a predefined value in the range of the registered ports
34. Compared to UDP, what factor causes additional network overhead for TCP communication?
- network traffic that is caused by retransmissions
- the identification of applications based on destination port numbers
- the encapsulation into IP packets
- the checksum error detection
35. Which transport layer feature is used to guarantee session establishment?
- UDP ACK flag
- TCP 3-way handshake
- UDP sequence number
- TCP port number
36. Which two flags in the TCP header are used in a TCP three-way handshake to establish connectivity between two network devices? (Choose two.)
- ACK
- FIN
- PSH
- RST
- SYN
- URG
37. Which factor determines TCP window size?
- the amount of data to be transmitted
- the number of services included in the TCP segment
- the amount of data the destination can process at one time
- the amount of data the source is capable of sending at one time
38. During a TCP session, a destination device sends an acknowledgment number to the source device. What does the acknowledgment number represent?
- the total number of bytes that have been received
- one number more than the sequence number
- the next byte that the destination expects to receive
- the last sequence number that was sent by the source
39. A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the server send before it requires an acknowledgment from the PC?
- 1 segment
- 10 segments
- 100 segments
- 1000 segments
40. Which two TCP header fields are used to confirm receipt of data?
- FIN flag
- SYN flag
- checksum
- sequence number
- acknowledgment number
41. What happens if the first packet of a TFTP transfer is lost?
- The client will wait indefinitely for the reply.
- The TFTP application will retry the request if a reply is not received.
- The next-hop router or the default gateway will provide a reply with an error code.
- The transport layer will retry the query if a reply is not received.
42. What does a client do when it has UDP datagrams to send?
- It just sends the datagrams.
- It queries the server to see if it is ready to receive data.
- It sends a simplified three-way handshake to the server.
- It sends to the server a segment with the SYN flag set to synchronize the conversation.
43. A technician wishes to use TFTP to transfer a large file from a file server to a remote router. Which statement is correct about this scenario?
- The file is segmented and then reassembled in the correct order by TCP.
- The file is segmented and then reassembled in the correct order at the destination, if necessary, by the upper-layer protocol.
- The file is not segmented, because UDP is the transport layer protocol that is used by TFTP.
- Large files must be sent by FTP not TFTP.
44. Fill in the blank.
During a TCP session, the SYN flag is used by the client to request communication with the server.
45. Fill in the blank using a number.
A total of 4 messages are exchanged during the TCP session termination process between the client and the server.
46. Refer to the exhibit. Consider a datagram that originates on the PC and that is destined for the web server. Match the IP addresses and port numbers that are in that datagram to the description. (Not all options are used.)
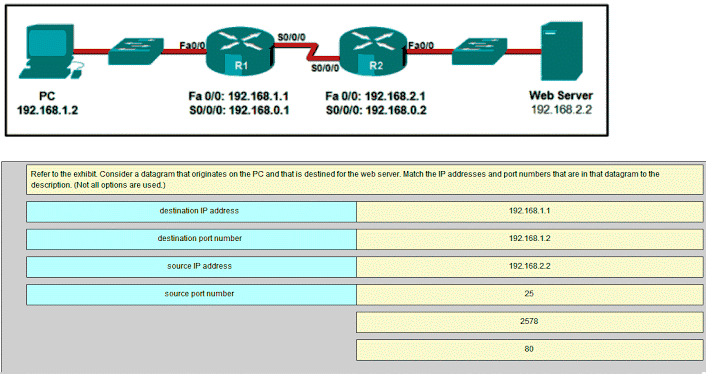
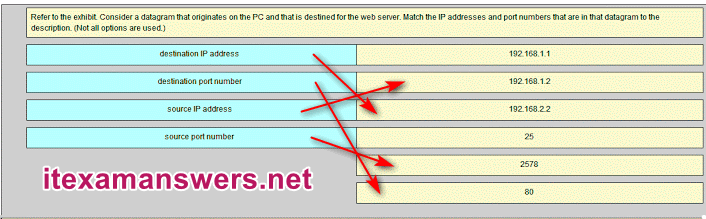
47. Match the characteristic to the protocol category. (Not all options are used.)
48. Match each application to its connectionless or connection-oriented protocol.
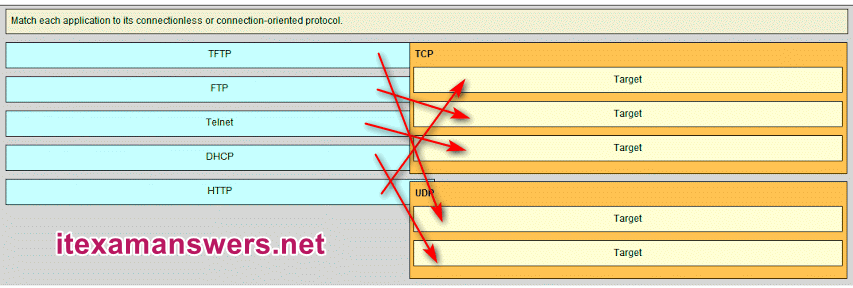
CCNA 1 – ITN Chapter 8 Exam Answers
1. What is a result of connecting two or more switches together?
- The number of broadcast domains is increased.
- The size of the broadcast domain is increased.
- The number of collision domains is reduced.
- The size of the collision domain is increased.
2. Refer to the exhibit. How many broadcast domains are there?
- 1
- 2
- 3
- 4
3. What are two reasons a network administrator might want to create subnets? (Choose two.)
- simplifies network design
- improves network performance
- easier to implement security policies
- reduction in number of routers needed
- reduction in number of switches needed
4. Refer to the exhibit. A company uses the address block of 128.107.0.0/16 for its network. What subnet mask would provide the maximum number of equal size subnets while providing enough host addresses for each subnet in the exhibit?
- 255.255.255.0
- 255.255.255.128
- 255.255.255.192
- 255.255.255.224
- 255.255.255.240
5. Refer to the exhibit. The network administrator has assigned the LAN of LBMISS an address range of 192.168.10.0. This address range has been subnetted using a /29 prefix. In order to accommodate a new building, the technician has decided to use the fifth subnet for configuring the new network (subnet zero is the first subnet). By company policies, the router interface is always assigned the first usable host address and the workgroup server is given the last usable host address. Which configuration should be entered into the properties of the workgroup server to allow connectivity to the Internet?
- IP address: 192.168.10.65 subnet mask: 255.255.255.240, default gateway: 192.168.10.76
- IP address: 192.168.10.38 subnet mask: 255.255.255.240, default gateway: 192.168.10.33
- IP address: 192.168.10.38 subnet mask: 255.255.255.248, default gateway: 192.168.10.33
- IP address: 192.168.10.41 subnet mask: 255.255.255.248, default gateway: 192.168.10.46
- IP address: 192.168.10.254 subnet mask: 255.255.255.0, default gateway: 192.168.10.1
6. If a network device has a mask of /28, how many IP addresses are available for hosts on this network?
- 256
- 254
- 62
- 32
- 16
- 14
7. Which subnet mask would be used if 5 host bits are available?
- 255.255.255.0
- 255.255.255.128
- 255.255.255.224
- 255.255.255.240
8. How many host addresses are available on the network 172.16.128.0 with a subnet mask of 255.255.252.0?
- 510
- 512
- 1022
- 1024
- 2046
- 2048
9. How many bits must be borrowed from the host portion of an address to accommodate a router with five connected networks?
- two
- three
- four
- five
10. A network administrator wants to have the same network mask for all networks at a particular small site. The site has the following networks and number of devices:
IP phones – 22 addresses
PCs – 20 addresses needed
Printers – 2 addresses needed
Scanners – 2 addresses needed
The network administrator has deemed that 192.168.10.0/24 is to be the network used at this site. Which single subnet mask would make the most efficient use of the available addresses to use for the four subnetworks?
- 255.255.255.0
- 255.255.255.192
- 255.255.255.224
- 255.255.255.240
- 255.255.255.248
- 255.255.255.252
11. A company has a network address of 192.168.1.64 with a subnet mask of 255.255.255.192. The company wants to create two subnetworks that would contain 10 hosts and 18 hosts respectively. Which two networks would achieve that? (Choose two.)
- 192.168.1.16/28
- 192.168.1.64/27
- 192.168.1.128/27
- 192.168.1.96/28
- 192.168.1.192/28
12. A network administrator is variably subnetting a network. The smallest subnet has a mask of 255.255.255.248. How many usable host addresses will this subnet provide?
- 4
- 6
- 8
- 10
- 12
13. Refer to the exhibit. Given the network address of 192.168.5.0 and a subnet mask of 255.255.255.224, how many total host addresses are unused in the assigned subnets?
- 56
- 60
- 64
- 68
- 72
14. Refer to the exhibit. Considering the addresses already used and having to remain within the 10.16.10.0/24 network range, which subnet address could be assigned to the network containing 25 hosts?
- 10.16.10.160/26
- 10.16.10.128/28
- 10.16.10.64/27
- 10.16.10.224/26
- 10.16.10.240/27
- 10.16.10.240/28
15. Refer to the exhibit. Given the network address of 192.168.5.0 and a subnet mask of 255.255.255.224 for all subnets, how many total host addresses are unused in the assigned subnets?
- 64
- 56
- 68
- 60
- 72
16. A network administrator needs to monitor network traffic to and from servers in a data center. Which features of an IP addressing scheme should be applied to these devices?
- random static addresses to improve security
- addresses from different subnets for redundancy
- predictable static IP addresses for easier identification
- dynamic addresses to reduce the probability of duplicate addresses
17. Which two reasons generally make DHCP the preferred method of assigning IP addresses to hosts on large networks? (Choose two.)
- It eliminates most address configuration errors.
- It ensures that addresses are only applied to devices that require a permanent address.
- It guarantees that every device that needs an address will get one.
- It provides an address only to devices that are authorized to be connected to the network.
- It reduces the burden on network support staff.
18. A DHCP server is used to assign IP addresses dynamically to the hosts on a network. The address pool is configured with 192.168.10.0/24. There are 3 printers on this network that need to use reserved static IP addresses from the pool. How many IP addresses in the pool are left to be assigned to other hosts?
- 254
- 251
- 252
- 253
19. Refer to the exhibit. A company is deploying an IPv6 addressing scheme for its network. The company design document indicates that the subnet portion of the IPv6 addresses is used for the new hierarchical network design, with the site subsection to represent multiple geographical sites of the company, the sub-site section to represent multiple campuses at each site, and the subnet section to indicate each network segment separated by routers. With such a scheme, what is the maximum number of subnets achieved per sub-site?
- 0
- 4
- 16
- 256
20. What is the prefix for the host address 2001:DB8:BC15:A:12AB::1/64?
- 2001:DB8:BC15
- 2001:DB8:BC15:A
- 2001:DB8:BC15:A:1
- 2001:DB8:BC15:A:12
21. Consider the following range of addresses:
2001:0DB8:BC15:00A0:0000::
2001:0DB8:BC15:00A1:0000::
2001:0DB8:BC15:00A2:0000::
2001:0DB8:BC15:00AF:0000::
The prefix-length for the range of addresses is /60
22. Match the subnetwork to a host address that would be included within the subnetwork. (Not all options are used.)
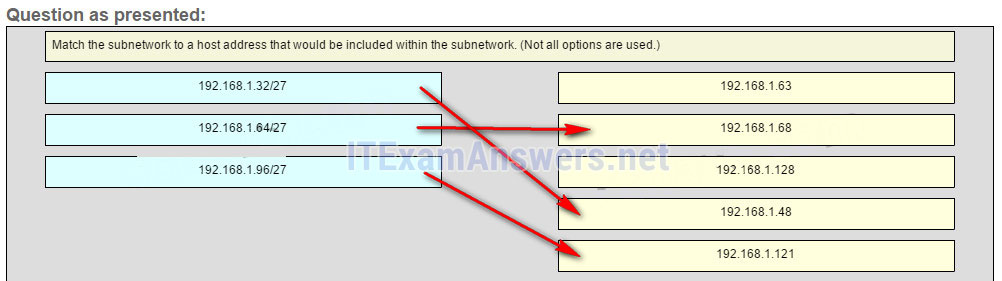
23. Refer to the exhibit. Match the network with the correct IP address and prefix that will satisfy the usable host addressing requirements for each network. (Not all options are used.) From right to left, network A has 100 hosts connected to the router on the right. The router on the right is connected via a serial link to the router on the left. The serial link represents network D with 2 hosts. The left router connects network B with 50 hosts and network C with 25 hosts.
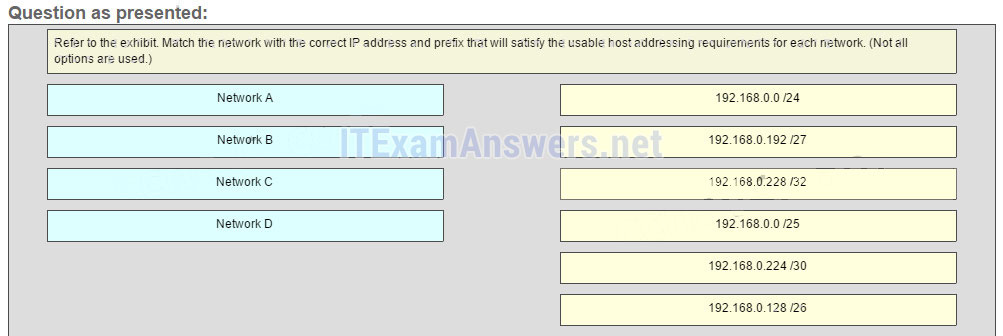
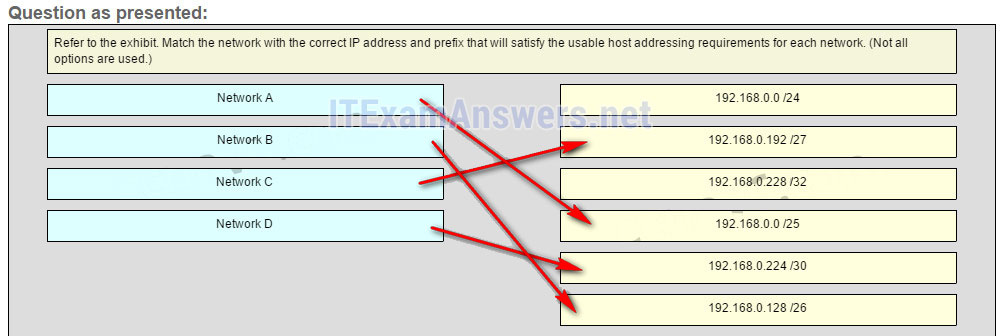
24. How many bits are in an IPv4 address?
- 32
- 64
- 128
- 256
25. Which two parts are components of an IPv4 address? (Choose two.)
- subnet portion
- network portion
- logical portion
- host portion
- physical portion
- broadcast portion
26. What is the prefix length notation for the subnet mask 255.255.255.224?
- /25
- /26
- /27
27. A message is sent to all hosts on a remote network. Which type of message is it?
- limited broadcast
- multicast
- directed broadcast
- unicast
28. What two statements describe characteristics of Layer 3 broadcasts? (Choose two.)
- Broadcasts are a threat and users must avoid using protocols that implement them.
- Routers create broadcast domains.
- Some IPv6 protocols use broadcasts.
- There is a broadcast domain on each switch interface.
- A limited broadcast packet has a destination IP address of 255.255.255.255.
- A router will not forward any type of Layer 3 broadcast packet.
29. Which network migration technique encapsulates IPv6 packets inside IPv4 packets to carry them over IPv4 network infrastructures?
- encapsulation
- translation
- dual-stack
- tunneling
30. Which two statements are correct about IPv4 and IPv6 addresses? (Choose two.)
- IPv6 addresses are represented by hexadecimal numbers.
- IPv4 addresses are represented by hexadecimal numbers.
- IPv6 addresses are 32 bits in length.
- IPv4 addresses are 32 bits in length.
- IPv4 addresses are 128 bits in length.
- IPv6 addresses are 64 bits in length.
31. Which IPv6 address is most compressed for the full FE80:0:0:0:2AA:FF:FE9A:4CA3 address?
- FE8::2AA:FF:FE9A:4CA3?
- FE80::2AA:FF:FE9A:4CA3
- FE80::0:2AA:FF:FE9A:4CA3?
- FE80:::0:2AA:FF:FE9A:4CA3?
32. What are two types of IPv6 unicast addresses? (Choose two.)
- multicast
- loopback
- link-local
- anycast
- broadcast
33. What are three parts of an IPv6 global unicast address? (Choose three.)
- an interface ID that is used to identify the local network for a particular host
- a global routing prefix that is used to identify the network portion of the address that has been provided by an ISP
- a subnet ID that is used to identify networks inside of the local enterprise site
- a global routing prefix that is used to identify the portion of the network address provided by a local administrator
- an interface ID that is used to identify the local host on the network
34. An IPv6 enabled device sends a data packet with the destination address of FF02::1. What is the target of this packet?
- all IPv6 DHCP servers
- all IPv6 enabled nodes on the local link
- all IPv6 configured routers on the local link
- all IPv6 configured routers across the network
35. When a Cisco router is being moved from an IPv4 network to a complete IPv6 environment, which series of commands would correctly enable IPv6 forwarding and interface addressing?
- Router# configure terminal
Router(config)# interface fastethernet 0/0
Router(config-if)# ip address 192.168.1.254 255.255.255.0
Router(config-if)# no shutdown
Router(config-if)# exit
Router(config)# ipv6 unicast-routing - Router# configure terminal
Router(config)# interface fastethernet 0/0
Router(config-if)# ipv6 address 2001:db8:bced:1::9/64
Router(config-if)# no shutdown
Router(config-if)# exit
Router(config)# ipv6 unicast-routing - Router# configure terminal
Router(config)# interface fastethernet 0/0
Router(config-if)# ipv6 address 2001:db8:bced:1::9/64
Router(config-if)# no shutdown - Router# configure terminal
Router(config)# interface fastethernet 0/0
Router(config-if)# ip address 2001:db8:bced:1::9/64
Router(config-if)# ip address 192.168.1.254 255.255.255.0
Router(config-if)# no shutdown
36. Which two ICMP messages are used by both IPv4 and IPv6 protocols? (Choose two.)?
- router solicitation
- route redirection
- neighbor solicitation
- protocol unreachable
- router advertisement
37. When an IPv6 enabled host needs to discover the MAC address of an intended IPv6 destination, which destination address is used by the source host in the NS message?
- all-node multicast address
- solicited-node multicast address
- link-local address of the receiver
- global unicast address of the receiver
38. When will a router drop a traceroute packet?
- when the router receives an ICMP Time Exceeded message
- when the RTT value reaches zero
- when the host responds with an ICMP Echo Reply message
- when the value in the TTL field reaches zero
- when the values of both the Echo Request and Echo Reply messages reach zero
39. What is indicated by a successful ping to the ::1 IPv6 address?
- The host is cabled properly.
- The default gateway address is correctly configured.
- All hosts on the local link are available.
- The link-local address is correctly configured.
- IP is properly installed on the host.
40. Which two things can be determined by using the ping command? (Choose two.)
- the number of routers between the source and destination device
- the IP address of the router nearest the destination device
- the average time it takes a packet to reach the destination and for the response to return to the source
- whether or not the destination device is reachable through the network
- the average time it takes each router in the path between source and destination to respond
41. Fill in the blank.
The decimal equivalent of the binary number 10010101 is 149
42. Fill in the blank.
What is the decimal equivalent of the hex number 0x3F? 63
43. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. Which message is displayed on the web server?
- You did it right!
- Correct configuration!
- IPv6 address configured!
- Successful configuration!
44. Match each IPv4 address to the appropriate address category. (Not all options are used.)
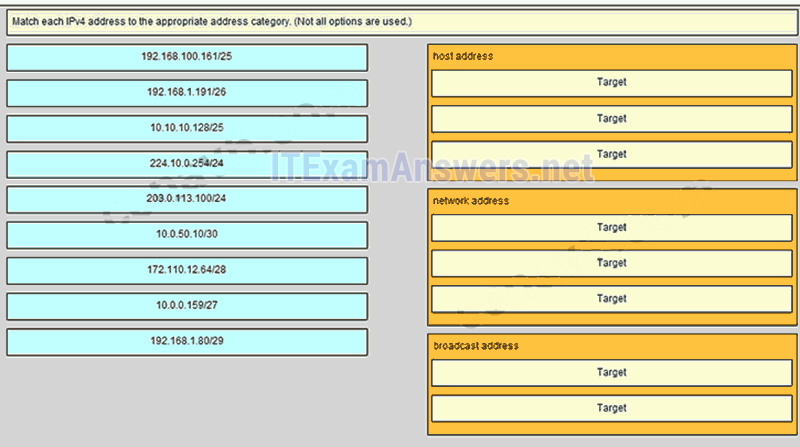
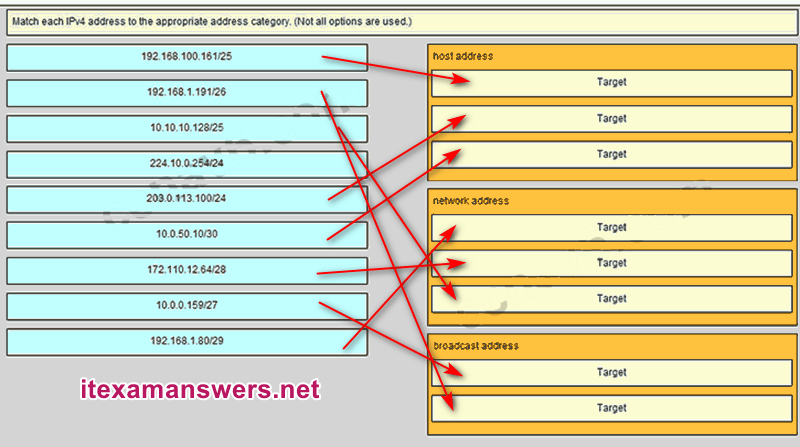
45. Match each description with an appropriate IP address. (Not all options are used)
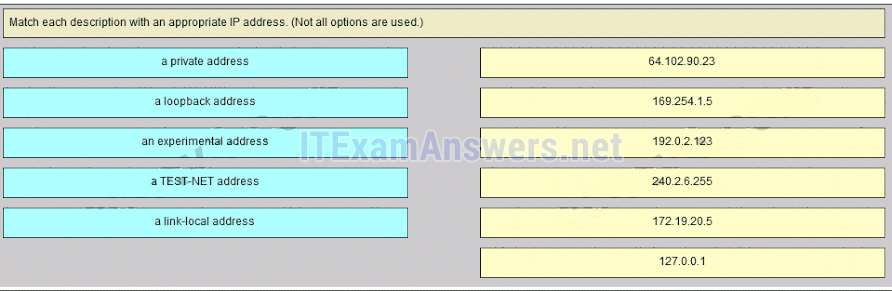
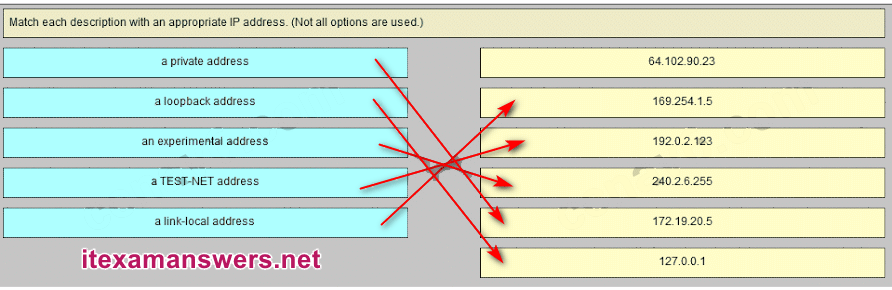
46. Match each description with an appropriate IP address. (Not all options are used.)
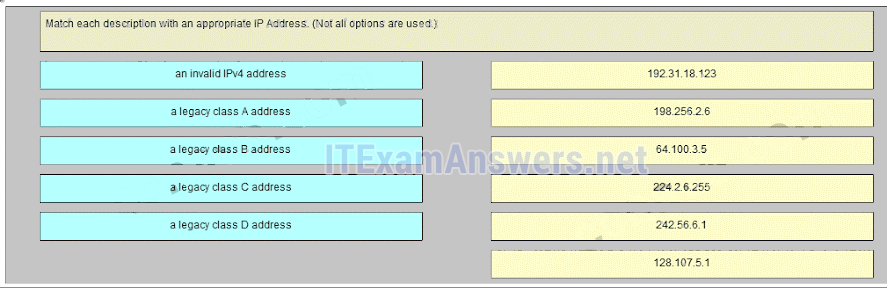
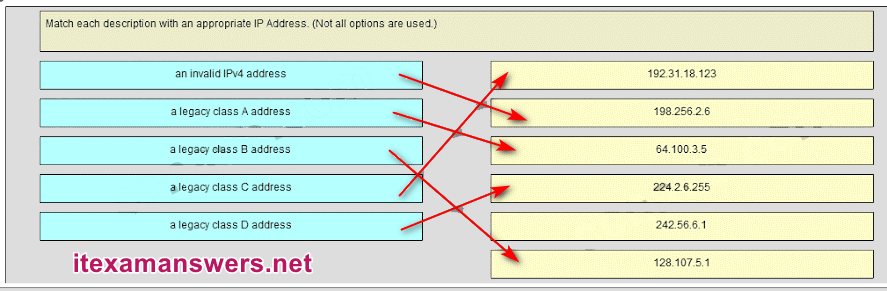
47. Which three addresses could be used as the destination address for OSPFv3 messages? (Choose three.)
- FF02::A
- FF02::1:2
- 2001:db8:cafe::1
- FE80::1
- FF02::5
- FF02::6
48. What is the result of connecting multiple switches to each other?
- The number of broadcast domains is increasing.
- The number of collision domains decreases.
- The size of the broadcast domain is increasing.
- The size of the collision domain decreases.
49. Which wildcard mask would be used to advertise the 192.168.5.96/27 network as part of an OSPF configuration?
- 255.255.255.224
- 0.0.0.32
- 255.255.255.223
- 0.0.0.31
50. Media description: An IPv6 network address with 64 bit network mask is shown. The first three blocks are 2001, DB8, and 1234. The fourth block shows four zeros. The first zero is labeled SIte, the second and third zeros are labeled together as Sub-site, the last zero is labeled Subnet.
Refer to the exhibit. A company is deploying an IPv6 addressing scheme for its network. The company design document indicates that the subnet portion of the IPv6 addresses is used for the new hierarchical network design, with the site subsection to represent multiple geographical sites of the company, the sub-site section to represent multiple campuses at each site, and the subnet section to indicate each network segment separated by routers. With such a scheme, what is the maximum number of subnetsachieved per sub-site?
- 4
- 16
- 256
- 0
CCNA 1 – ITN Chapter 9 Exam Answers
1. Which two characteristics are associated with UDP sessions? (Choose two.)
- Destination devices receive traffic with minimal delay.
- Transmitted data segments are tracked.
- Destination devices reassemble messages and pass them to an application.
- Received data is unacknowledged.
- Unacknowledged data packets are retransmitted.
2. What happens if part of an FTP message is not delivered to the destination?
- The message is lost because FTP does not use a reliable delivery method.
- The FTP source host sends a query to the destination host.
- The part of the FTP message that was lost is re-sent.
- The entire FTP message is re-sent.
3. A host device needs to send a large video file across the network while providing data communication to other users. Which feature will allow different communication streams to occur at the same time, without having a single data stream using all available bandwidth?
- window size
- multiplexing
- port numbers
- acknowledgments
4. What kind of port must be requested from IANA in order to be used with a specific application?
- registered port
- private port
- dynamic port
- source port
5. What type of information is included in the transport header?
- destination and source logical addresses
- destination and source physical addresses
- destination and source port numbers
- encoded application data
6. What is a socket?
- the combination of the source and destination IP address and source and destination Ethernet address
- the combination of a source IP address and port number or a destination IP address and port number
- the combination of the source and destination sequence and acknowledgment numbers
- the combination of the source and destination sequence numbers and port numbers
7. What is the complete range of TCP and UDP well-known ports?
- 0 to 255
- 0 to 1023
- 256 – 1023
- 1024 – 49151
8. Which flag in the TCP header is used in response to a received FIN in order to terminate connectivity between two network devices?
- FIN
- ACK
- SYN
- RST
9. What is a characteristic of a TCP server process?
- Every application process running on the server has to be configured to use a dynamic port number.
- There can be many ports open simultaneously on a server, one for each active server application.
- An individual server can have two services assigned to the same port number within the same transport layer services.
- A host running two different applications can have both configured to use the same server port.
10. Which two flags in the TCP header are used in a TCP three-way handshake to establish connectivity between two network devices? (Choose two.)
- ACK
- FIN
- PSH
- RST
- SYN
- URG
11. A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the server send before it requires an acknowledgment from the PC?
- 1 segment
- 10 segments
- 100 segments
- 1000 segments
12. Which factor determines TCP window size?
- the amount of data to be transmitted
- the number of services included in the TCP segment
- the amount of data the destination can process at one time
- the amount of data the source is capable of sending at one time
13. During a TCP session, a destination device sends an acknowledgment number to the source device. What does the acknowledgment number represent?
- the total number of bytes that have been received
- one number more than the sequence number
- the next byte that the destination expects to receive
- the last sequence number that was sent by the source
14. What information is used by TCP to reassemble and reorder received segments?
- port numbers
- sequence numbers
- acknowledgment numbers
- fragment numbers
15. What does TCP do if the sending source detects network congestion on the path to the destination?
- The source host will send a request for more frequent acknowledgments to the destination.
- The source will decrease the amount of data that it sends before it must receive acknowledgements from the destination.
- The destination will request retransmission of the entire message.
- The source will acknowledge the last segment that is sent and include a request for a smaller window size in the message.
16. What is a characteristic of UDP?
- UDP datagrams take the same path and arrive in the correct order at the destination.
- Applications that use UDP are always considered unreliable.
- UDP reassembles the received datagrams in the order they were received.
- UDP only passes data to the network when the destination is ready to receive the data.
17. What does a client do when it has UDP datagrams to send?
- It just sends the datagrams.
- It queries the server to see if it is ready to receive data.
- It sends a simplified three-way handshake to the server.
- It sends to the server a segment with the SYN flag set to synchronize the conversation.
18. What happens if the first packet of a TFTP transfer is lost?
- The client will wait indefinitely for the reply.
- The TFTP application will retry the request if a reply is not received.
- The next-hop router or the default gateway will provide a reply with an error code.
- The transport layer will retry the query if a reply is not received.
19. A host device is receiving live streaming video. How does the device account for video data that is lost during transmission?
- The device will immediately request a retransmission of the missing data.
- The device will use sequence numbers to pause the video stream until the correct data arrives.
- The device will delay the streaming video until the entire video stream is received.
- The device will continue receiving the streaming video, but there may be a momentary disruption.
20. Why does HTTP use TCP as the transport layer protocol?
- to ensure the fastest possible download speed
- because HTTP is a best-effort protocol
- because transmission errors can be tolerated easily
- because HTTP requires reliable delivery
21. When is UDP preferred to TCP?
- when a client sends a segment to a server
- when all the data must be fully received before any part of it is considered useful
- when an application can tolerate some loss of data during transmission
- when segments must arrive in a very specific sequence to be processed successfully
22. Which three application layer protocols use TCP? (Choose three.)
- SMTP
- FTP
- SNMP
- HTTP
- TFTP
- DHCP
23. Refer to the exhibit. Consider a datagram that originates on the PC and that is destined for the web server. Match the IP addresses and port numbers that are in that datagram to the description. (Not all options are used.)
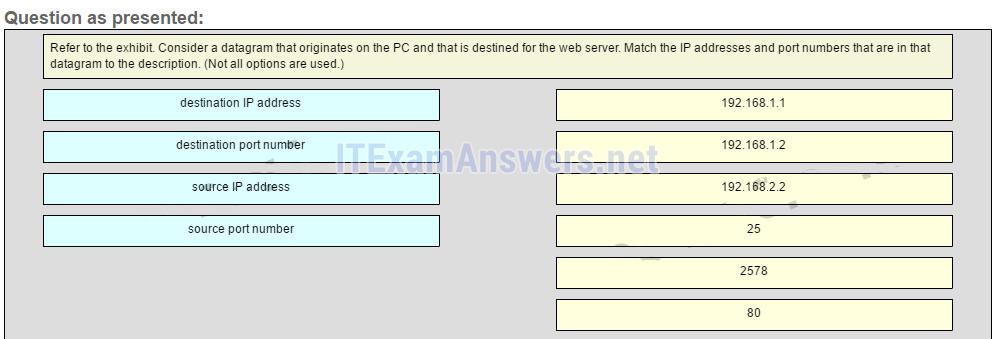
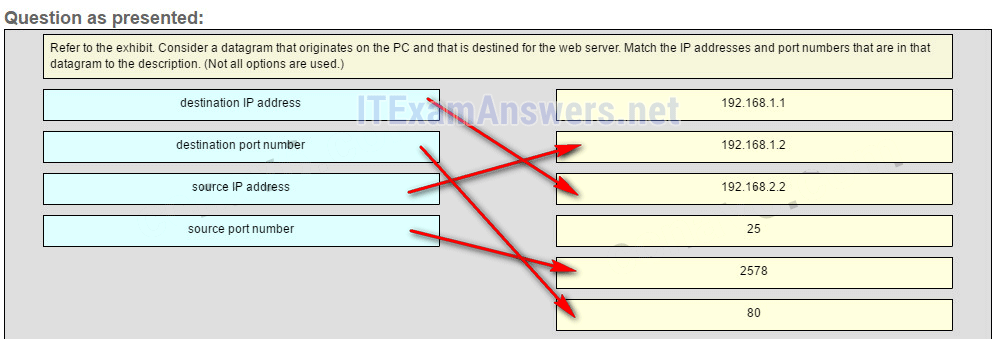
24. What information is used by TCP to reassemble and reorder received segments?
- sequence numbers
- acknowledgment numbers
- fragment numbers
- port numbers
25. Refer to the exhibit. How many broadcast domains are there?
- 1
- 2
- 3
- 4
26. How many usable host addresses are there in the subnet 192.168.1.32/27?
- 32
- 30
- 64
- 16
- 62
27. How many host addresses are available on the network 172.16.128.0 with a subnet mask of 255.255.252.0?
- 510
- 512
- 1022
- 1024
- 2046
- 2048
28. A network administrator is variably subnetting a network. The smallest subnet has a mask of 255.255.255.248. How many host addresses will this subnet provide?
- 4
- 6
- 8
- 10
- 12
29. Refer to the exhibit. A company uses the address block of 128.107.0.0/16 for its network. What subnet mask would provide the maximum number of equal size subnets while providing enough host addresses for each subnet in the exhibit?
- 255.255.255.0
- 255.255.255.128
- 255.255.255.192
- 255.255.255.224
- 255.255.255.240
30. Refer to the exhibit. The network administrator has assigned the LAN of LBMISS an address range of 192.168.10.0. This address range has been subnetted using a /29 prefix. In order to accommodate a new building, the technician has decided to use the fifth subnet for configuring the new network (subnet zero is the first subnet). By company policies, the router interface is always assigned the first usable host address and the workgroup server is given the last usable host address. Which configuration should be entered into the properties of the workgroup server to allow connectivity to the Internet?
- IP address: 192.168.10.65 subnet mask: 255.255.255.240, default gateway: 192.168.10.76
- IP address: 192.168.10.38 subnet mask: 255.255.255.240, default gateway: 192.168.10.33
- IP address: 192.168.10.38 subnet mask: 255.255.255.248, default gateway: 192.168.10.33
- IP address: 192.168.10.41 subnet mask: 255.255.255.248, default gateway: 192.168.10.46
- IP address: 192.168.10.254 subnet mask: 255.255.255.0, default gateway: 192.168.10.1
31. How many bits must be borrowed from the host portion of an address to accommodate a router with five connected networks?
- two
- three
- four
- five
32. A company has a network address of 192.168.1.64 with a subnet mask of 255.255.255.192. The company wants to create two subnetworks that would contain 10 hosts and 18 hosts respectively. Which two networks would achieve that? (Choose two.)
- 192.168.1.16/28
- 192.168.1.64/27
- 192.168.1.128/27
- 192.168.1.96/28
- 192.168.1.192/28
33. In a network that uses IPv4, what prefix would best fit a subnet containing 100 hosts?
- /23
- /24
- /25
- /26
34. Refer to the exhibit.
Given the network address of 192.168.5.0 and a subnet mask of 255.255.255.224, how many total host addresses are unused in the assigned subnets?
- 56
- 60
- 64
- 68
- 72
35. When developing an IP addressing scheme for an enterprise network, which devices are recommended to be grouped into their own subnet or logical addressing group?
- end-user clients
- workstation clients
- mobile and laptop hosts
- hosts accessible from the Internet
36. A network administrator needs to monitor network traffic to and from servers in a data center. Which features of an IP addressing scheme should be applied to these devices?
- random static addresses to improve security
- addresses from different subnets for redundancy
- predictable static IP addresses for easier identification
- dynamic addresses to reduce the probability of duplicate addresses
37. Which two reasons generally make DHCP the preferred method of assigning IP addresses to hosts on large networks? (Choose two.)
- It eliminates most address configuration errors.
- It ensures that addresses are only applied to devices that require a permanent address.
- It guarantees that every device that needs an address will get one.
- It provides an address only to devices that are authorized to be connected to the network.
- It reduces the burden on network support staff.
38. Refer to the exhibit. A computer that is configured with the IPv6 address as shown in the exhibit is unable to access the internet. What is the problem?
- The DNS address is wrong.
- There should not be an alternative DNS address.
- The gateway address is in the wrong subnet.
- The settings were not validated.
39. When subnetting a /64 IPv6 network prefix, which is the preferred new prefix length?
- /66
- /70
- /72
- /74
40. What is the subnet address for the address 2001:DB8:BC15:A:12AB::1/64?
- 2001:DB8:BC15::0
- 2001:DB8:BC15:A::0
- 2001:DB8:BC15:A:1::1
- 2001:DB8:BC15:A:12::0
41. Which two notations are useable nibble boundaries when subnetting in IPv6? (Choose two.)
- /62
- /64
- /66
- /68
- /70
42. Fill in the blank.
In dotted decimal notation, the IP address 172.25.0.126 is the last host address for the network 172.25.0.64/26.
43. Fill in the blank.
In dotted decimal notation, the subnet mask 255.255.254.0 will accommodate 500 hosts per subnet.
Consider the following range of addresses:
44. Fill in the blank.
A nibble consists of 4 bits.
45. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. What issue is causing Host A to be unable to communicate with Host B?
- The subnet mask of host A is incorrect.
- Host A has an incorrect default gateway.
- Host A and host B are on overlapping subnets.
- The IP address of host B is not in the same subnet as the default gateway is on.
46. Refer to the exhibit. Given the network address of 192.168.5.0 and a subnet mask of 255.255.255.224, how many addresses are wasted in total by subnetting each network with a subnet mask of 255.255.255.224?
- 56
- 60
- 64
- 68
- 72
47. Match the subnetwork to a host address that would be included within the subnetwork. (Not all options are used.)
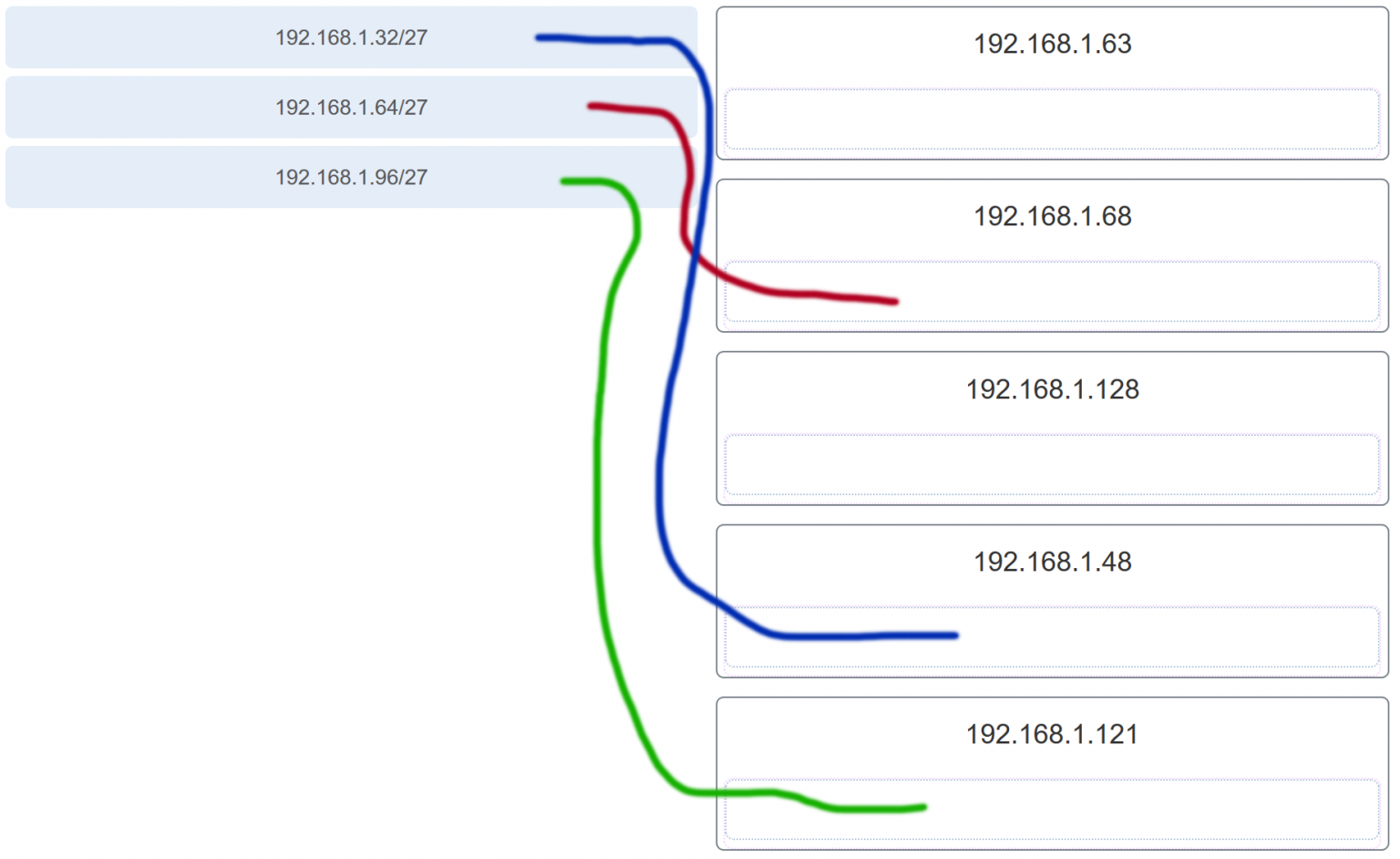
48. Refer to the exhibit. Match the network with the correct IP address and prefix that will satisfy the usable host addressing requirements for each network. (Not all options are used.)
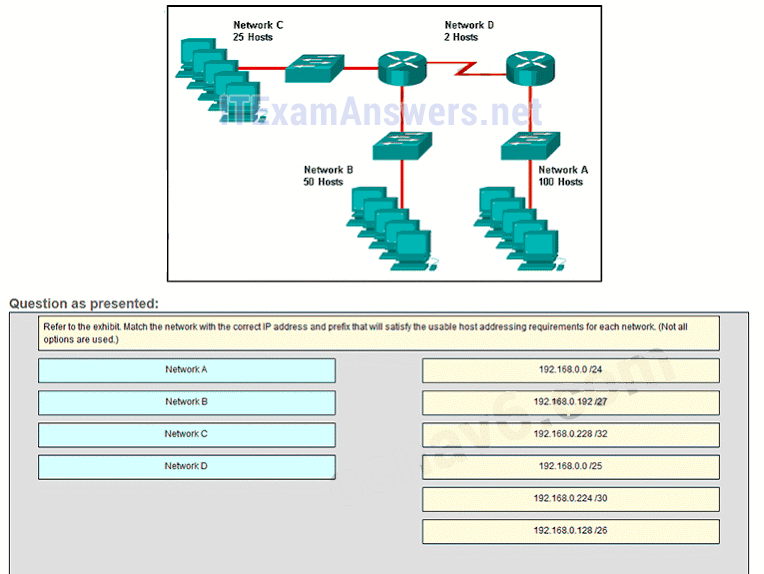
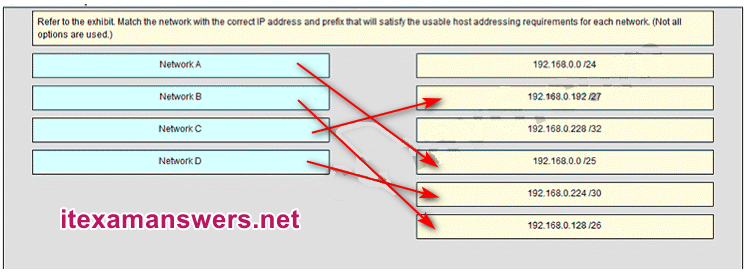
49. Which three features can be configured in the BIOS settings to secure a computer? (Choose three.)
- MAC filtering
- drive encryption
- TPM
- file encryption
- TKIP key
- passwords
50. Refer to the exhibit. A network administrator has configured OSPFv2 on the two Cisco routers. The routers are unable to form a neighbor adjacency. What should be done to fix the problem on router R2?
- Implement the command no passive-interface Serial0/1.
- Implement the command network 192.168.2.6 0.0.0.0 area 0 on router R2.
- Change the router-id of router R2 to 2.2.2.2.
- Implement the command network 192.168.3.1 0.0.0.0 area 0 on router R2.
CCNA 1 – ITN Chapter 10 Exam Answers
1. Which two definitions accurately describe the associated application layer protocol? (Choose two.)
- SMTP – transfers web pages from web servers to clients
- Telnet – provides remote access to servers and networking devices
- DNS – resolves Internet names to IP addresses
- FTP – transfers email messages and attachments
- HTTP – enables devices on a network to obtain IP addresses
2. The application layer of the TCP/IP model performs the functions of what three layers of the OSI model? (Choose three.)
- physical
- session
- network
- presentation
- data link
- transport
- application
3. Which layer in the TCP/IP model is used for formatting, compressing, and encrypting data?
- internetwork
- session
- presentation
- application
- network access
4. What are two characteristics of the application layer of the TCP/IP model? (Choose two.)
- responsibility for logical addressing
- responsibility for physical addressing
- the creation and maintenance of dialogue between source and destination applications
- closest to the end user
- the establishing of window size
5. A manufacturing company subscribes to certain hosted services from its ISP. The services that are required include hosted world wide web, file transfer, and e-mail. Which protocols represent these three key applications? (Choose three.)
- FTP
- HTTP
- DNS
- SNMP
- DHCP
- SMTP
6. What is an example of network communication that uses the client-server model?
- A user uses eMule to download a file that is shared by a friend after the file location is determined.
- A workstation initiates an ARP to find the MAC address of a receiving host.
- A user prints a document by using a printer that is attached to a workstation of a coworker.
- A workstation initiates a DNS request when the user types www.cisco.com in the address bar of a web browser.
7. Two students are working on a network design project. One student is doing the drawing, while the other student is writing the proposal. The drawing is finished and the student wants to share the folder that contains the drawing so that the other student can access the file and copy it to a USB drive. Which networking model is being used?
- peer-to-peer
- client-based
- master-slave
- point-to-point
8. What do the client/server and peer-to-peer network models have in common?
- Both models have dedicated servers.
- Both models support devices in server and client roles.
- Both models require the use of TCP/IP-based protocols.
- Both models are used only in the wired network environment.
9. What is an advantage for small organizations of adopting IMAP instead of POP?
- Messages are kept in the mail servers until they are manually deleted from the email client.
- When the user connects to a POP server, copies of the messages are kept in the mail server for a short time, but IMAP keeps them for a long time.
- IMAP sends and retrieves email, but POP only retrieves email.
- POP only allows the client to store messages in a centralized way, while IMAP allows distributed storage.
10. Which application layer protocol uses message types such as GET, PUT, and POST?
- DNS
- DHCP
- SMTP
- HTTP
- POP3
11. When retrieving email messages, which protocol allows for easy, centralized storage and backup of emails that would be desirable for a small- to medium-sized business?
- IMAP
- POP
- SMTP
- HTTPS
12. What is the function of the Nslookup utility?
- to manually query the name servers to resolve a given host name
- to view the network settings on a host
- to manually force a client to send a DHCP request
- to display all cached DNS entries on a host
13. What message type is used by an HTTP client to request data from a web server?
- POST
- ACK
- GET
- PUT
14. Which protocol is used by a client to communicate securely with a web server?
- SMB
- HTTPS
- SMTP
- IMAP
15. Which three statements describe a DHCP Discover message? (Choose three.)
- The source MAC address is 48 ones (FF-FF-FF-FF-FF-FF).
- The destination IP address is 255.255.255.255.
- The message comes from a server offering an IP address.
- The message comes from a client seeking an IP address.
- All hosts receive the message, but only a DHCP server replies.
- Only the DHCP server receives the message.
16. What part of the URL, http://www.cisco.com/index.html, represents the top-level DNS domain?
- .com
- www
- http
- index
17. Which two tasks can be performed by a local DNS server? (Choose two.)
- providing IP addresses to local hosts
- allowing data transfer between two network devices
- mapping name-to-IP addresses for internal hosts
- forwarding name resolution requests between servers
- retrieving email messages
18. Which phrase describes an FTP daemon?
- a diagnostic FTP program
- a program that is running on an FTP server
- a program that is running on an FTP client
- an application that is used to request data from an FTP server
19. Which statement is true about FTP?
- The client can choose if FTP is going to establish one or two connections with the server.
- The client can download data from or upload data to the server.
- FTP is a peer-to-peer application.
- FTP does not provide reliability during data transmission.
20. What is true about the Server Message Block protocol?
- Different SMB message types have a different format.
- Clients establish a long term connection to servers.
- SMB messages cannot authenticate a session.
- SMB uses the FTP protocol for communication.
21. Which application layer protocol is used to provide file-sharing and print services to Microsoft applications?
- HTTP
- SMTP
- DHCP
- SMB
Explain:
SMB is used in Microsoft networking for file-sharing and print services. The Linux operating system provides a method of sharing resources with Microsoft networks by using a version of SMB called SAMBA.
22. Fill in the blank.
What is the acronym for the protocol that is used when securely communicating with a web server? HTTPS
23. Fill in the blank.
The HTTP message type used by the client to request data from the web server is the GET message.
24. Open the PT Activity.
Perform the tasks in the activity instructions and then answer the question.Which PC or PCs are sending FTP packets to the server?
- PC_3
- PC_1
- PC_2
- PC_1 and PC_3
25. Fill in the blank.
Refer to the exhibit. What command was used to resolve a given host name by querying the name servers?
nslookup
26. Match a statement to the related network model. (Not all options are used.)
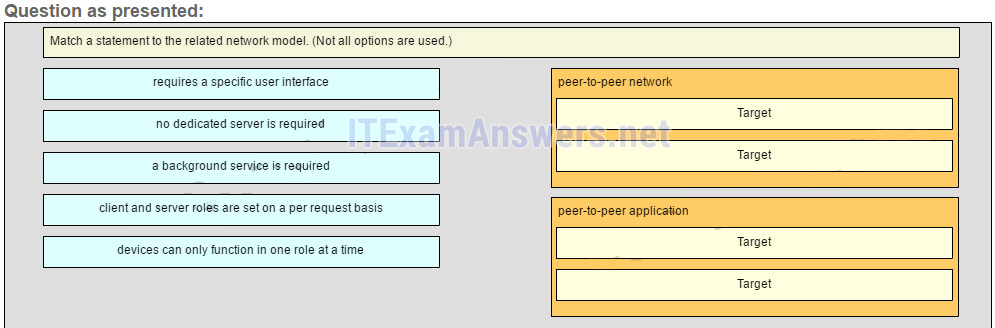
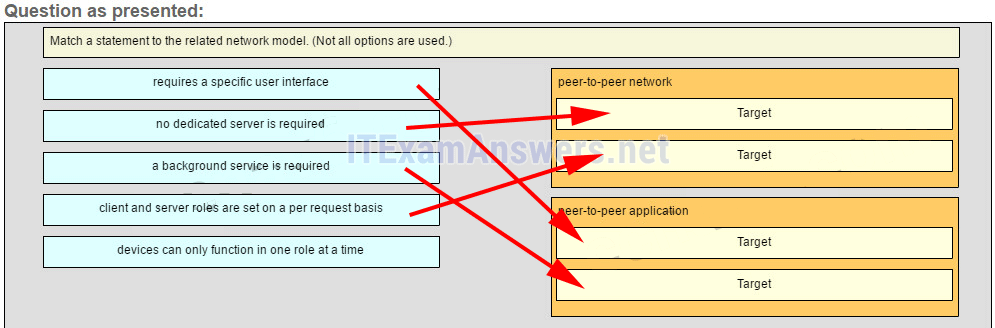
27. Match the functions to the name of the application. (Not all options are used.)
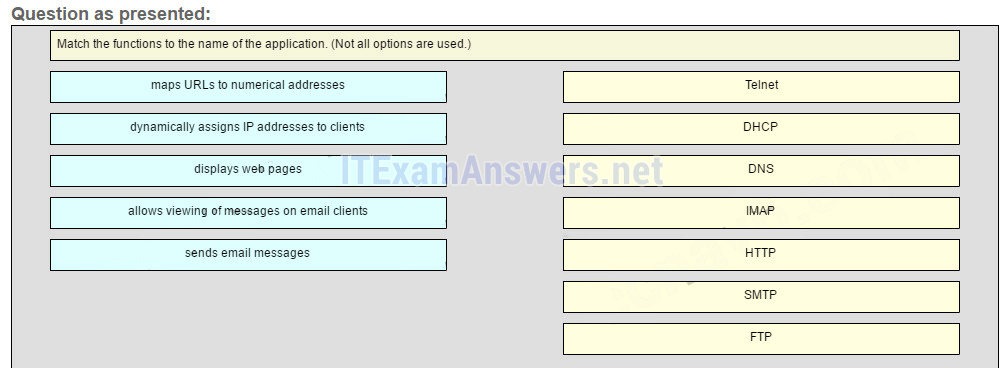
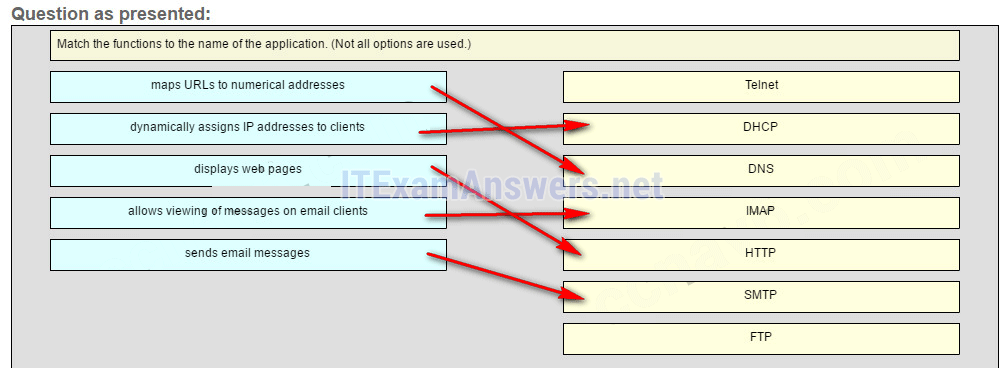
28. Which three layers of the OSI model provide similar network services to those provided by the application layer of the TCP/IP model? (Choose three.)
- physical layer
- session layer
- transport layer
- application layer
- presentation layer
- data link layer
29. Which two tasks are functions of the presentation layer? (Choose two.)
- compression
- addressing
- encryption
- session control
- authentication
30. Select three protocols that operate at the Application Layer of the OSI model. (Choose three.)
- ARP
- TCP
- DSL
- FTP
- POP3
- DHCP
31. A manufacturing company subscribes to certain hosted services from their ISP. The services required include hosted world wide web, file transfer, and e-mail. Which protocols represent these three key applications? (Choose three.)
32. What are two characteristics of peer-to-peer networks? (Choose two.)
- scalable
- one way data flow
- decentralized resources
- centralized user accounts
- resource sharing without a dedicated server
33. Which two actions are taken by SMTP if the destination email server is busy when email messages are sent? (Choose two.)
- SMTP sends an error message back to the sender and closes the connection.
- SMTP tries to send the messages at a later time.
- SMTP will discard the message if it is still not delivered after a predetermined expiration time.
- SMTP periodically checks the queue for messages and attempts to send them again.
- SMTP sends the messages to another mail server for delivery.
34. A DHCP-enabled client PC has just booted. During which two steps will the client PC use broadcast messages when communicating with a DHCP server? (Choose two.)
- DHCPDISCOVER
- DHCPACK
- DHCPOFFER
- DHCPREQUEST
- DHCPNAK
35. A user accessed the game site www.nogamename.com last week. The night before the user accesses the game site again, the site administrator changes the site IP address. What will be the consequence of that action for the user?
- The user will not be able to access the site.
- The user will access the site without problems.
- The user will have to modify the DNS server address on the local PC in order to access the site.
- The user will have to issue a ping to this new IP address to be sure that the domain name remained the same.
36. Which DNS server in the DNS hierarchy would be considered authoritative for the domain name records of a company named netacad?
- .com
- netacad.com
- mx.netacad.com
- www.netacad.com
37. When would it be more efficient to use SMB to transfer files instead of FTP?
- when downloading large files with a variety of formats from different servers
- when a peer-to-peer application is required
- when the host devices on the network use the Windows operating system
- when downloading large numbers of files from the same server
- when uploading the same file to multiple remote servers
38. Fill in the blank.
What is the acronym for the protocol that is used when securely communicating with a web server? HTTPS
39. Match the DNS record type to the corresponding description. (Not all options are used.)
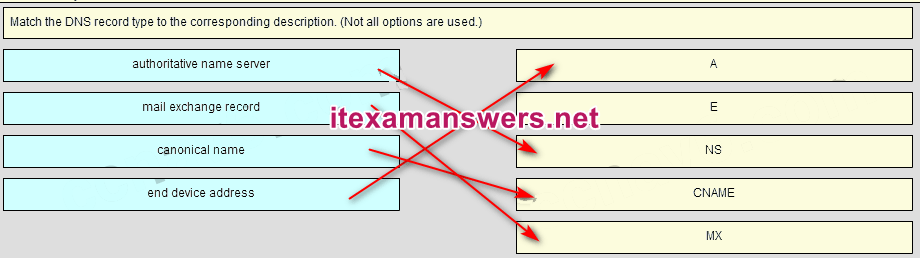
40. Match the purpose with its DHCP message type. (Not all options are used.)
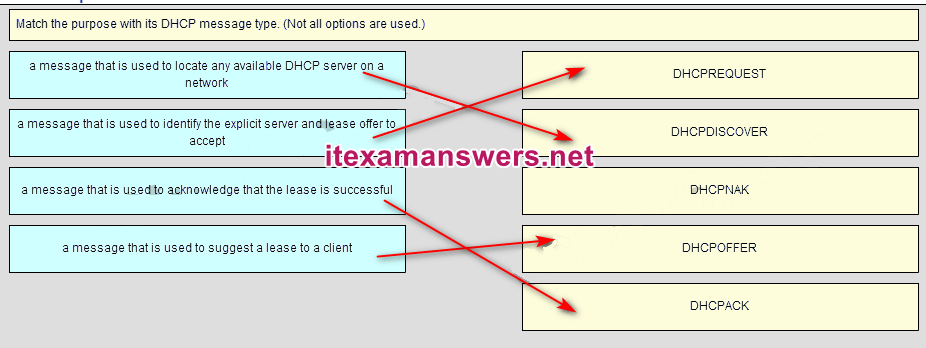
41. Open the PT activity. Perform the tasks in the activity instructions and then answer the question.
What is the application layer service being requested from Server0 by PC0?
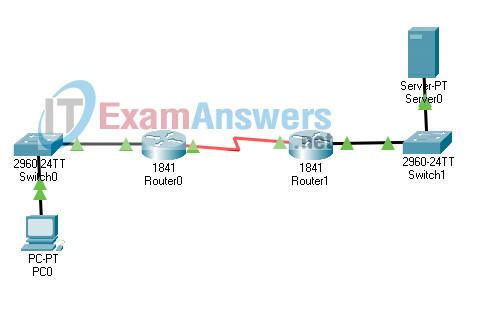
In the Simulation mode, capture the packets. What is the application layer service being requested from Server0 by PC0?
Return to the assessment to answer the question.
- FTP
- DNS
- HTTPS
- HTTP
- SMTP
42. Which protocol is used by Windows for file and printer sharing?
- SMB
- SMTP
- HTTPS
- IMAP
CCNA 1 – ITN Chapter 11 Exam Answers
1. A newly hired network technician is given the task of ordering new hardware for a small business with a large growth forecast. Which primary factor should the technician be concerned with when choosing the new devices?
- devices with a fixed number and type of interfaces
- devices that have support for network monitoring
- redundant devices
- devices with support for modularity
2. Which network design consideration would be more important to a large corporation than to a small business?
- Internet router
- firewall
- low port density switch
- redundancy
3. Which two traffic types require delay sensitive delivery? (Choose two.)
- web
- FTP
- voice
- video
4. A network administrator for a small company is contemplating how to scale the network over the next three years to accommodate projected growth. Which three types of information should be used to plan for network growth? (Choose three.)
- human resource policies and procedures for all employees in the company
- documentation of the current physical and logical topologies
- analysis of the network traffic based on protocols, applications, and services used on the network
- history and mission statement of the company
- inventory of the devices that are currently used on the network
- listing of the current employees and their role in the company
5. Which two statements describe how to assess traffic flow patterns and network traffic types using a protocol analyzer? (Choose two.)
- Capture traffic on the weekends when most employees are off work.
- Only capture traffic in the areas of the network that receive most of the traffic such as the data center.
- Capture traffic during peak utilization times to get a good representation of the different traffic types.
- Perform the capture on different network segments.
- Only capture WAN traffic because traffic to the web is responsible for the largest amount of traffic on a network.
6. Some routers and switches in a wiring closet malfunctioned after an air conditioning unit failed. What type of threat does this situation describe?
- configuration
- environmental
- electrical
- maintenance
7. Which type of network threat is intended to prevent authorized users from accessing resources?
- DoS attacks
- access attacks
- reconnaissance attacks
- trust exploitation
8. Which two actions can be taken to prevent a successful network attack on an email server account? (Choose two.)
- Never send the password through the network in a clear text.
- Never use passwords that need the Shift key.
- Use servers from different vendors.
- Distribute servers throughout the building, placing them close to the stakeholders.
- Limit the number of unsuccessful attempts to log in to the server.
9. Which firewall feature is used to ensure that packets coming into a network are legitimate responses initiated from internal hosts?
- application filtering
- stateful packet inspection
- URL filtering
- packet filtering
10. What is the purpose of the network security authentication function?
- to require users to prove who they are
- to determine which resources a user can access
- to keep track of the actions of a user
- to provide challenge and response questions
11. A network administrator is issuing the login block-for 180 attempts 2 within 30 command on a router. Which threat is the network administrator trying to prevent?
- a user who is trying to guess a password to access the router
- a worm that is attempting to access another part of the network
- an unidentified individual who is trying to access the network equipment room
- a device that is trying to inspect the traffic on a link
12. Which two steps are required before SSH can be enabled on a Cisco router? (Choose two.)
- Give the router a host name and domain name.
- Create a banner that will be displayed to users when they connect.
- Generate a set of secret keys to be used for encryption and decryption.
- Set up an authentication server to handle incoming connection requests.
- Enable SSH on the physical interfaces where the incoming connection requests will be received.
13. Refer to the exhibit. Baseline documentation for a small company had ping round trip time statistics of 36/97/132 between hosts H1 and H3. Today the network administrator checked connectivity by pinging between hosts H1 and H3 that resulted in a round trip time of 1458/2390/6066. What does this indicate to the network administrator?
- Connectivity between H1 and H3 is fine.
- H3 is not connected properly to the network.
- Something is causing interference between H1 and R1.
- Performance between the networks is within expected parameters.
- Something is causing a time delay between the networks.
14. When should an administrator establish a network baseline?
- when the traffic is at peak in the network
- when there is a sudden drop in traffic
- at the lowest point of traffic in the network
- at regular intervals over a period of time
15. Refer to the exhibit. An administrator is trying to troubleshoot connectivity between PC1 and PC2 and uses the tracert command from PC1 to do it. Based on the displayed output, where should the administrator begin troubleshooting?
- PC2
- R1
- SW2
- R2
- SW1
16. Which statement is true about CDP on a Cisco device?
- The show cdp neighbor detail command will reveal the IP address of a neighbor only if there is Layer 3 connectivity.
- To disable CDP globally, the no cdp enable command in interface configuration mode must be used.
- CDP can be disabled globally or on a specific interface.
- Because it runs at the data link layer, the CDP protocol can only be implemented in switches.
17. A network administrator for a small campus network has issued the show ip interface brief command on a switch. What is the administrator verifying with this command?
- the status of the switch interfaces and the address configured on interface vlan 1
- that a specific host on another network can be reached
- the path that is used to reach a specific host on another network
- the default gateway that is used by the switch
18. A network technician issues the arp -d * command on a PC after the router that is connected to the LAN is reconfigured. What is the result after this command is issued?
- The ARP cache is cleared.
- The current content of the ARP cache is displayed.
- The detailed information of the ARP cache is displayed.
- The ARP cache is synchronized with the router interface.
19. Fill in the blank.
VoIP defines the protocols and technologies that implement the transmission of voice data over an IP network
20. Fill in the blank. Do not use abbreviations.
The show file systems command provides information about the amount of free nvram and flash memory with the permissions for reading or writing data.
21. Fill in the blank. Do not use abbreviations.
The show version command that is issued on a router is used to verify the value of the software configuration register.
22. What service defines the protocols and technologies that implement the transmission of voice packets over an IP network?
- VoIP
- NAT
- DHCP
- QoS
23. What is the purpose of using SSH to connect to a router?
- It allows a secure remote connection to the router command line interface.
- It allows a router to be configured using a graphical interface.
- It allows the router to be monitored through a network management application.
- It allows secure transfer of the IOS software image from an unsecure workstation or server.
24. What information about a Cisco router can be verified using the show version command?
- the value of the configuration register
- the administrative distance used to reach networks
- the operational status of serial interfaces
- the routing protocol version that is enabled
25. A network technician issues the C:\> tracert -6 www.cisco.com command on a Windows PC. What is the purpose of the -6 command option?
- It forces the trace to use IPv6.
- It limits the trace to only 6 hops.
- It sets a 6 milliseconds timeout for each replay.
- It sends 6 probes within each TTL time period.
26. Which command should be used on a Cisco router or switch to allow log messages to be displayed on remotely connected sessions using Telnet or SSH?
- debug all
- logging synchronous
- show running-config
- terminal monitor
27. Match the type of information security threat to the scenario. (Not all options are used.)
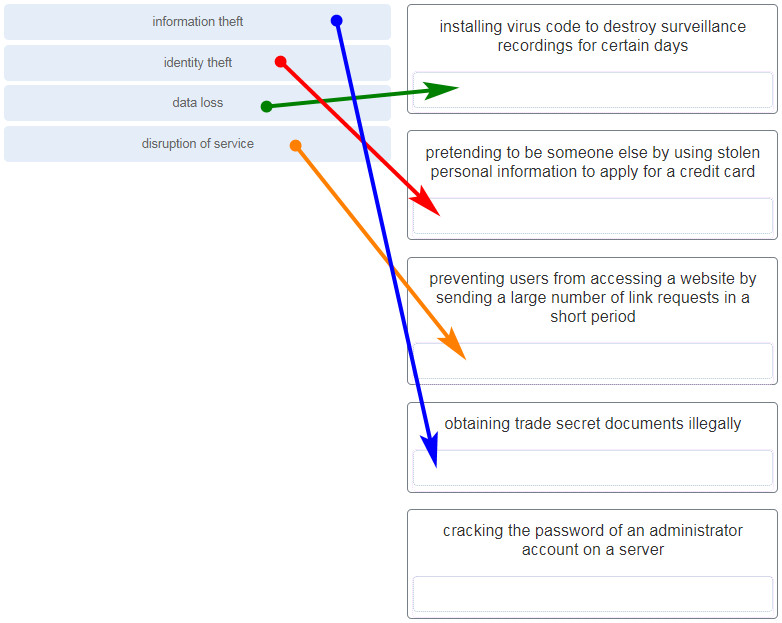
28. What is the purpose of issuing the commands cd nvram: then dir at the privilege exec mode of a router?
- to clear the content of the NVRAM
- to direct all new files to the NVRAM
- to list the content of the NVRAM
- to copy the directories from the NVRAM
29. Which command will backup the configuration that is stored in NVRAM to a TFTP server?
- copy running-config tftp
- copy tftp running-config
- copy startup-config tftp
- copy tftp startup-config
30. Which protocol supports rapid delivery of streaming media?
- SNMP
- TCP
- PoE
- RTP
31. How should traffic flow be captured in order to best understand traffic patterns in a network?
- during low utilization times
- during peak utilization times
- when it is on the main network segment only
- when it is from a subset of users
32. A network administrator checks the security log and notices there was unauthorized access to an internal file server over the weekend. Upon further investigation of the file system log, the administrator notices several important documents were copied to a host located outside of the company. What kind of threat is represented in this scenario?
- data loss
- identity theft
- information theft
- disruption of service
33. Which two actions can be taken to prevent a successful attack on an email server account? (Choose two.)
- Never send the password through the network in a clear text.
- Never use passwords that need the Shift key.
- Never allow physical access to the server console.
- Only permit authorized access to the server room.
- Limit the number of unsuccessful attempts to log in to the server.
34. Which type of network attack involves the disabling or corruption of networks, systems, or services?
- reconnaissance attacks
- access attacks
- denial of service attacks
- malicious code attacks
35. A network administrator has determined that various computers on the network are infected with a worm. Which sequence of steps should be followed to mitigate the worm attack?
- inoculation, containment, quarantine, and treatment
- containment, quarantine, treatment, and inoculation
- treatment, quarantine, inoculation, and containment
- containment, inoculation, quarantine, and treatment
36. What is a security feature of using NAT on a network?
- allows external IP addresses to be concealed from internal users
- allows internal IP addresses to be concealed from external users
- denies all packets that originate from private IP addresses
- denies all internal hosts from communicating outside their own network
37. A ping fails when performed from router R1 to directly connected router R2. The network administrator then proceeds to issue the show cdp neighbors command. Why would the network administrator issue this command if the ping failed between the two routers?
- The network administrator suspects a virus because the ping command did not work.
- The network administrator wants to verify Layer 2 connectivity.
- The network administrator wants to verify the IP address configured on router R2.
- The network administrator wants to determine if connectivity can be established from a non-directly connected network.
38. If a configuration file is saved to a USB flash drive attached to a router, what must be done by the network administrator before the file can be used on the router?
- Convert the file system from FAT32 to FAT16.
- Edit the configuration file with a text editor.
- Change the permission on the file from ro to rw.
- Use the dir command from the router to remove the Windows automatic alphabetization of the files on the flash drive.
39. Which two statements about a service set identifier (SSID) are true? (Choose two.)
- tells a wireless device to which WLAN it belongs
- consists of a 32-character string and is not case sensitive
- responsible for determining the signal strength
- all wireless devices on the same WLAN must have the same SSID
- used to encrypt data sent across the wireless network
40. What do WLANs that conform to IEEE 802.11 standards allow wireless users to do?
- use wireless mice and keyboards
- create a one-to-many local network using infrared technology
- use cell phones to access remote services over very large areas
- connect wireless hosts to hosts or services on a wired Ethernet network
41. Which WLAN security protocol generates a new dynamic key each time a client establishes a connection with the AP?
- EAP
- PSK
- WEP
- WPA
42. Which two statements characterize wireless network security? (Choose two.)
- Wireless networks offer the same security features as wired networks.
- Some RF channels provide automatic encryption of wireless data.
- With SSID broadcast disabled, an attacker must know the SSID to connect.
- Using the default IP address on an access point makes hacking easier.
- An attacker needs physical access to at least one network device to launch an attack.
43. Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. How long will a user be blocked if the user exceeds the maximum allowed number of unsuccessful login attempts?
- 1 minute
- 2 minutes
- 3 minutes
- 4 minutes


